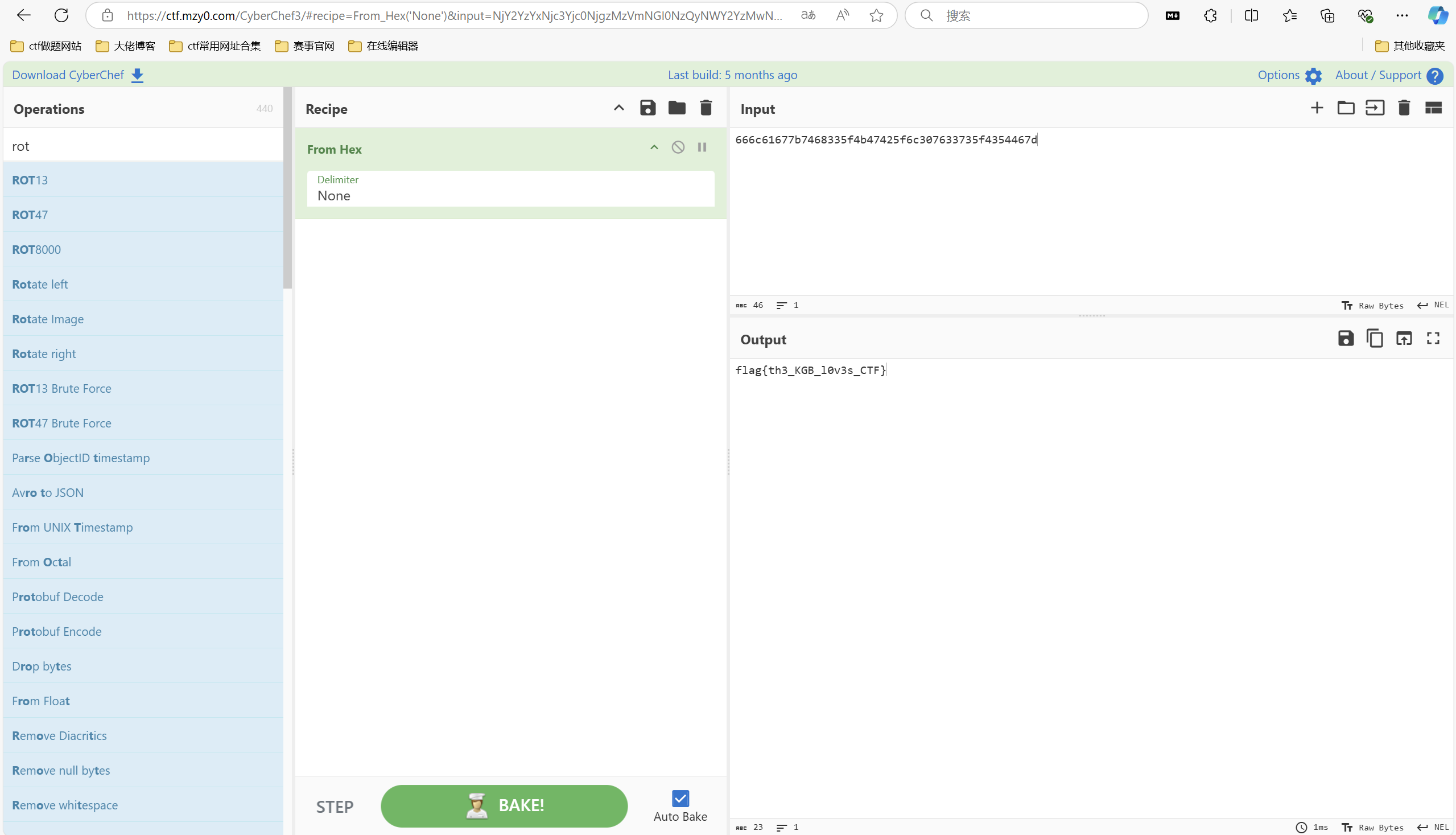
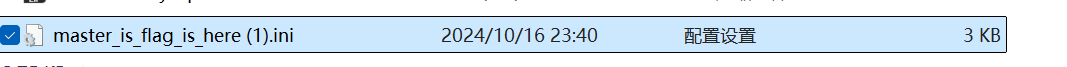题目附件:
1 2 3 4 通过百度网盘分享的文件:御宛题.zip 链接:https://pan.baidu.com/s/1i15jdms-Min9xmeDqasKkw?pwd=1fge 提取码:1fge --来自百度网盘超级会员V3的分享
MIISC 我敲,黑客
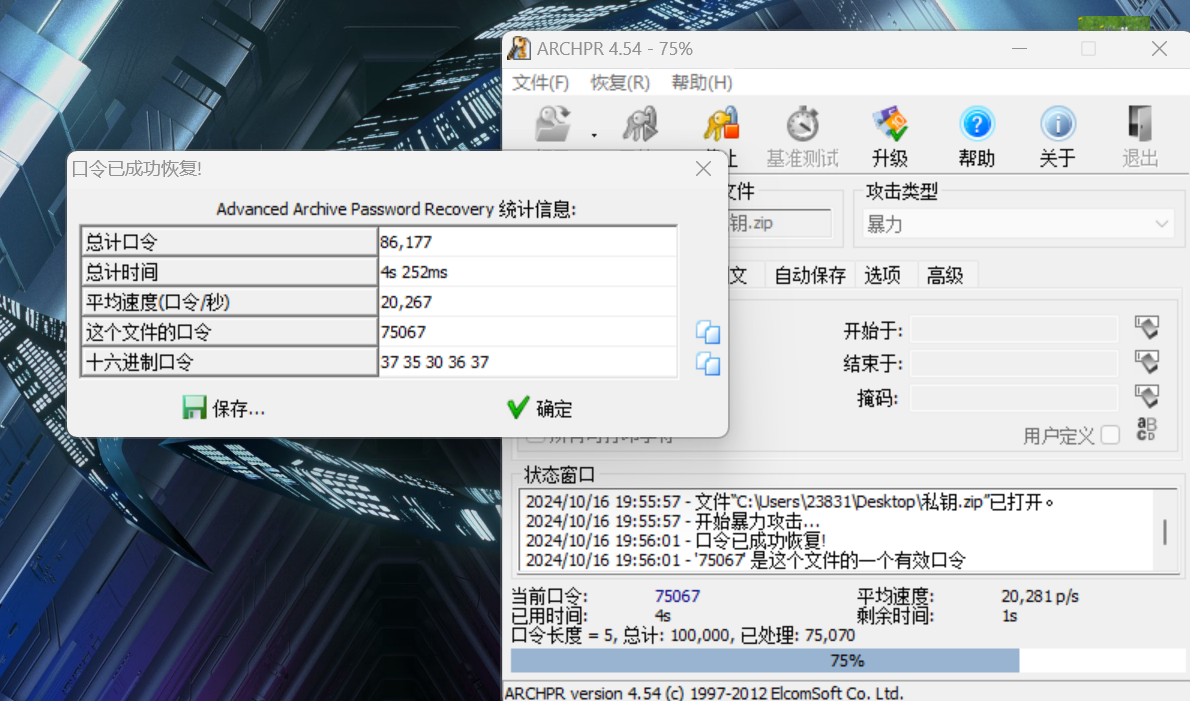
1 2 3 4 5 6 7 from Crypto.Util.number import * res = 0 for i in range(100,1000): if isPrime(i): res+=i print(res) # 75067
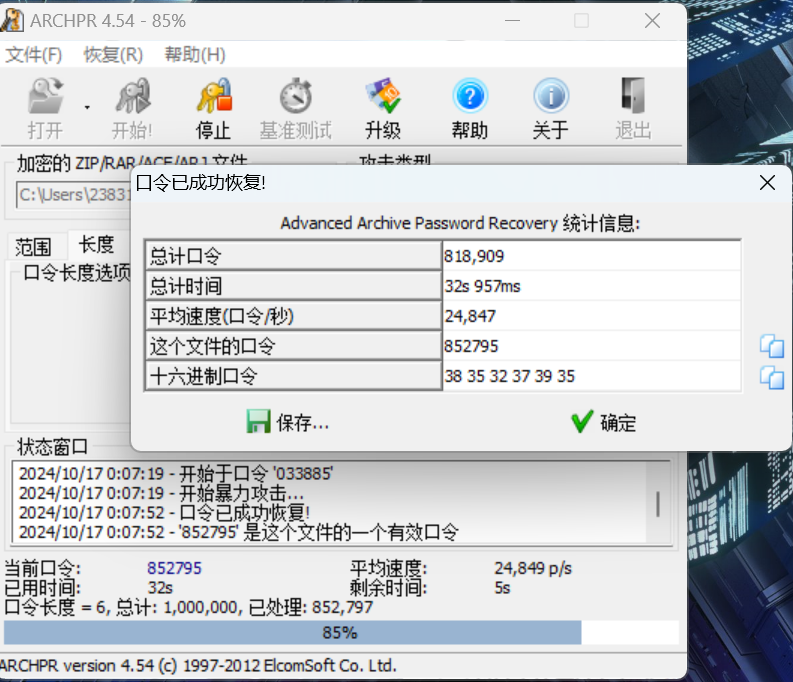
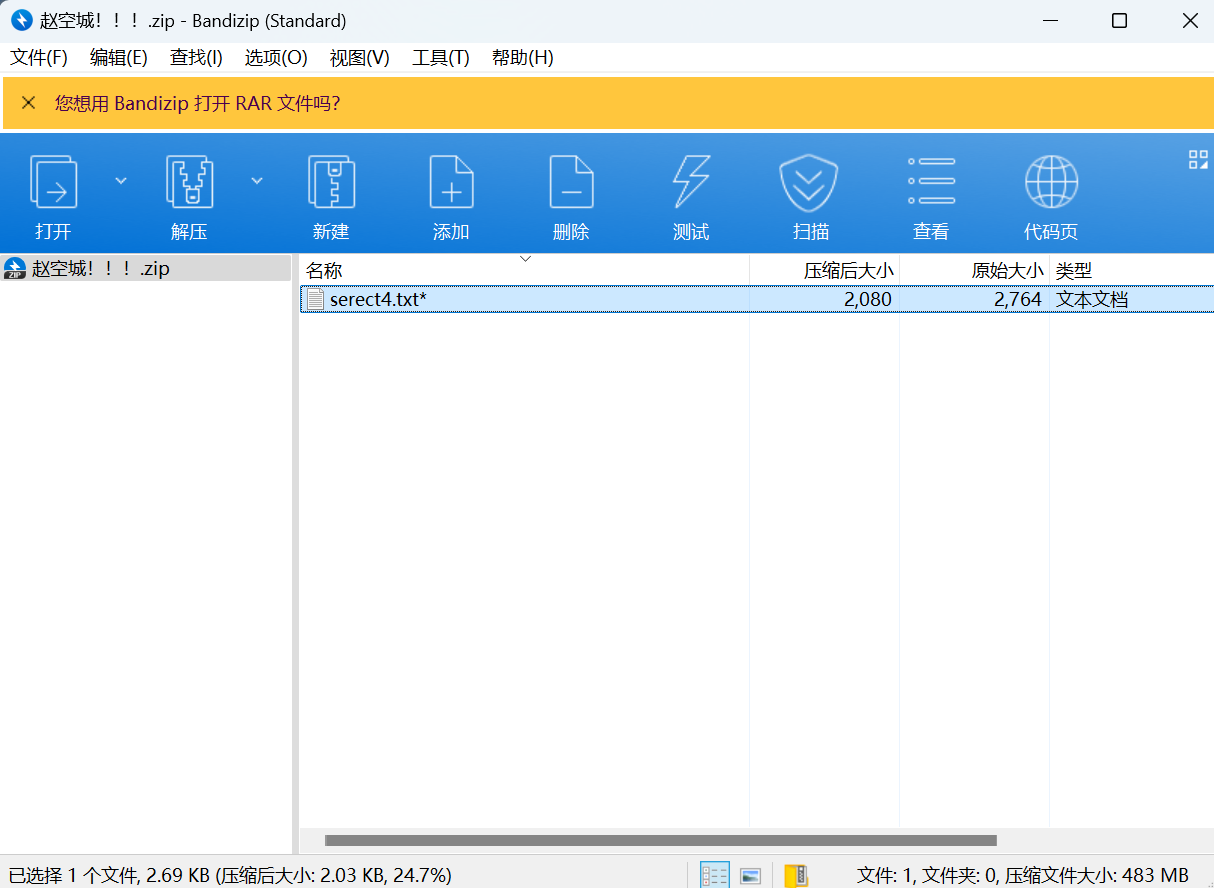
或者直接爆破密码
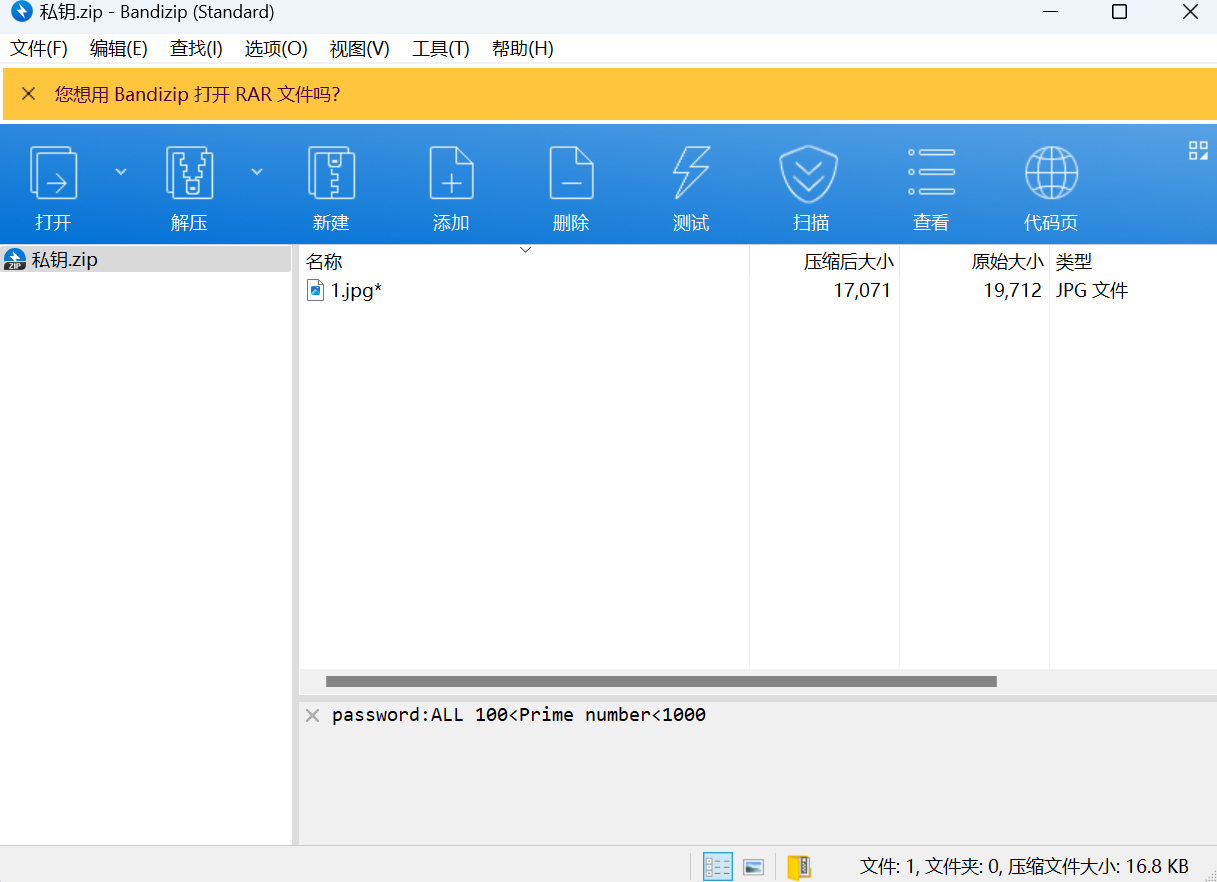
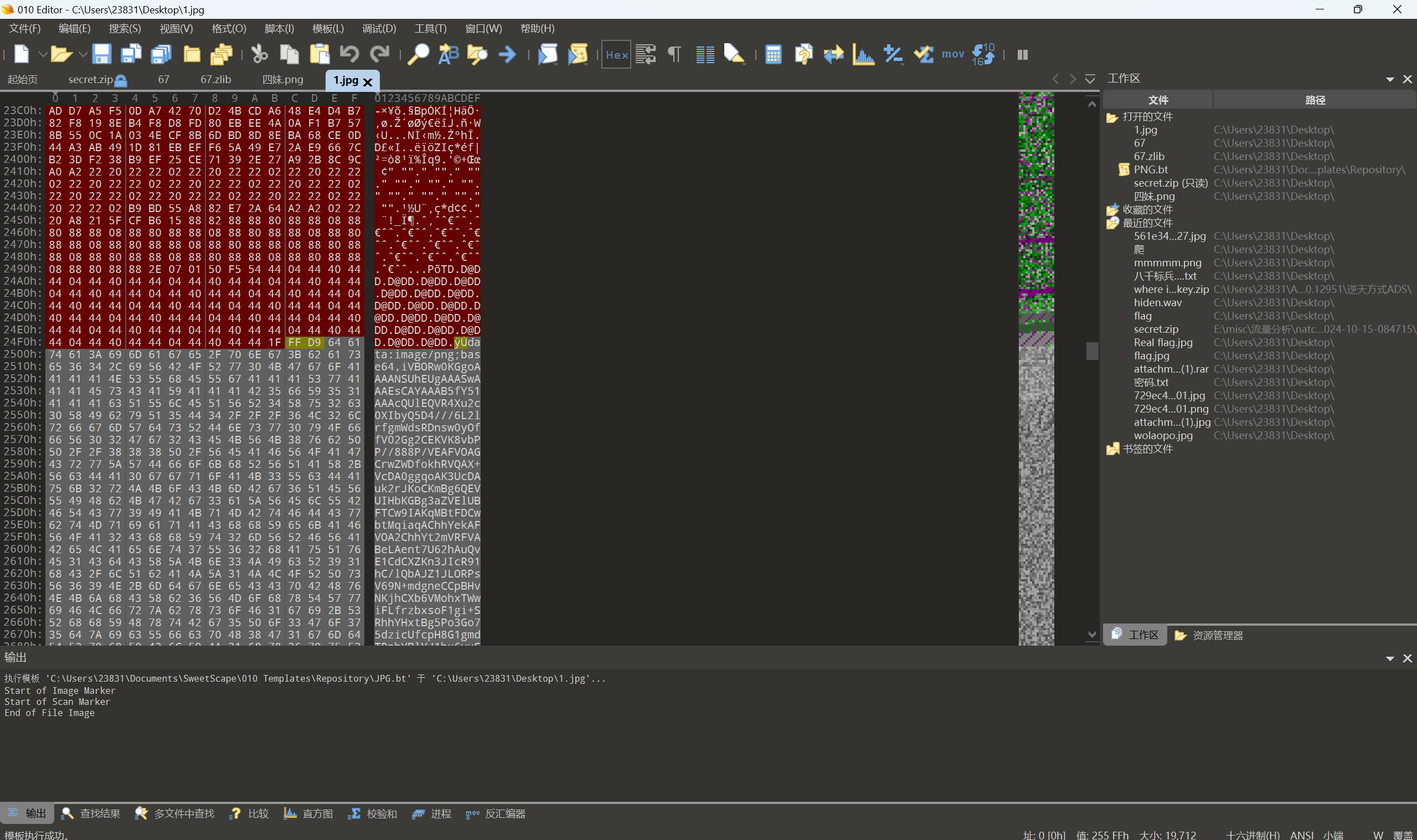
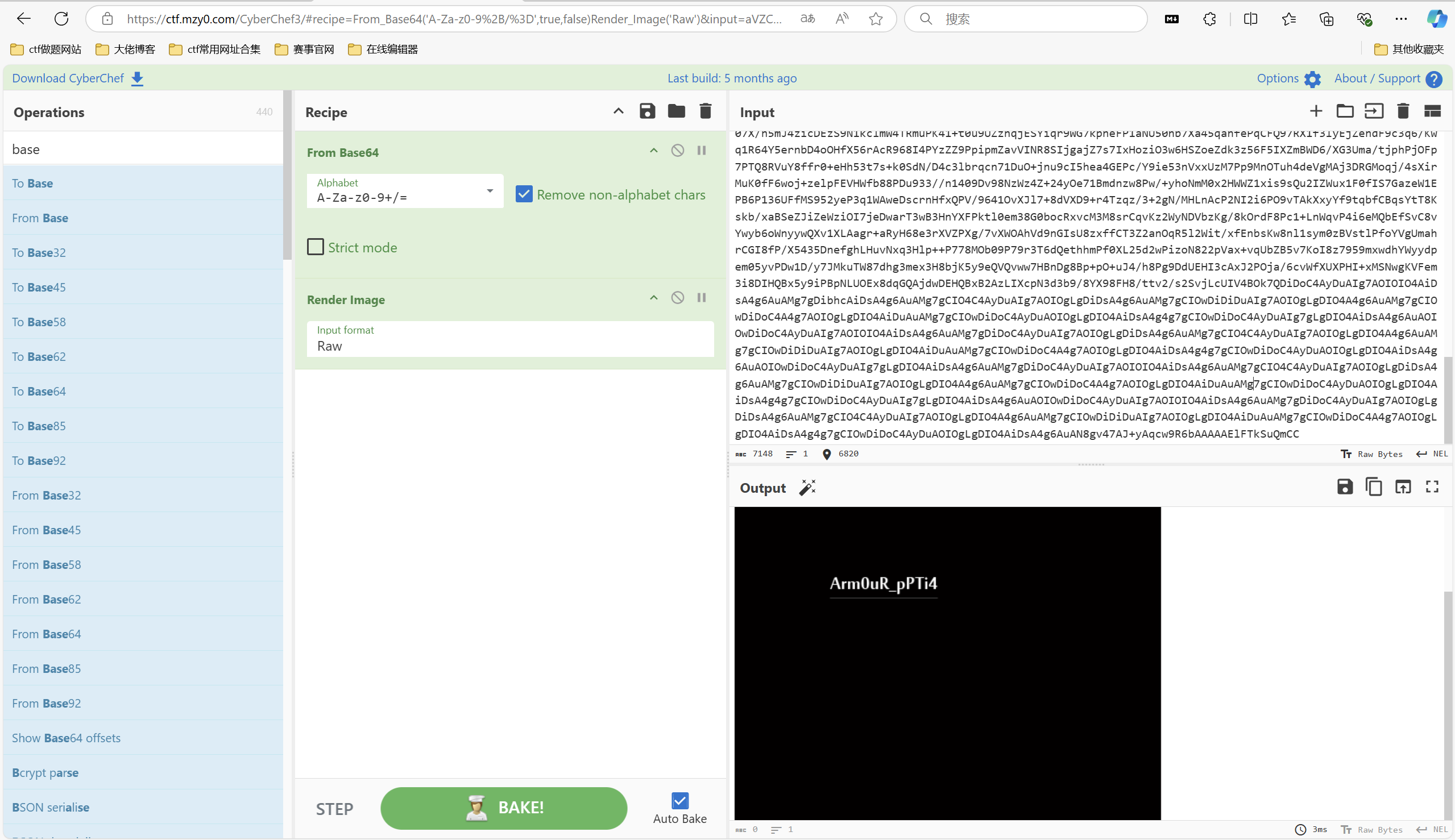
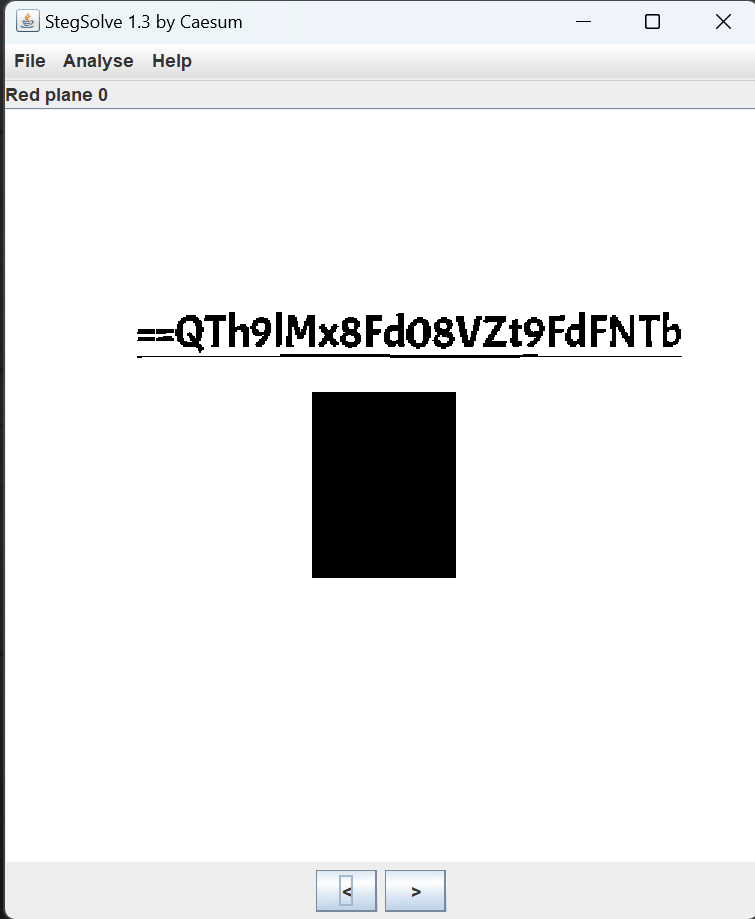
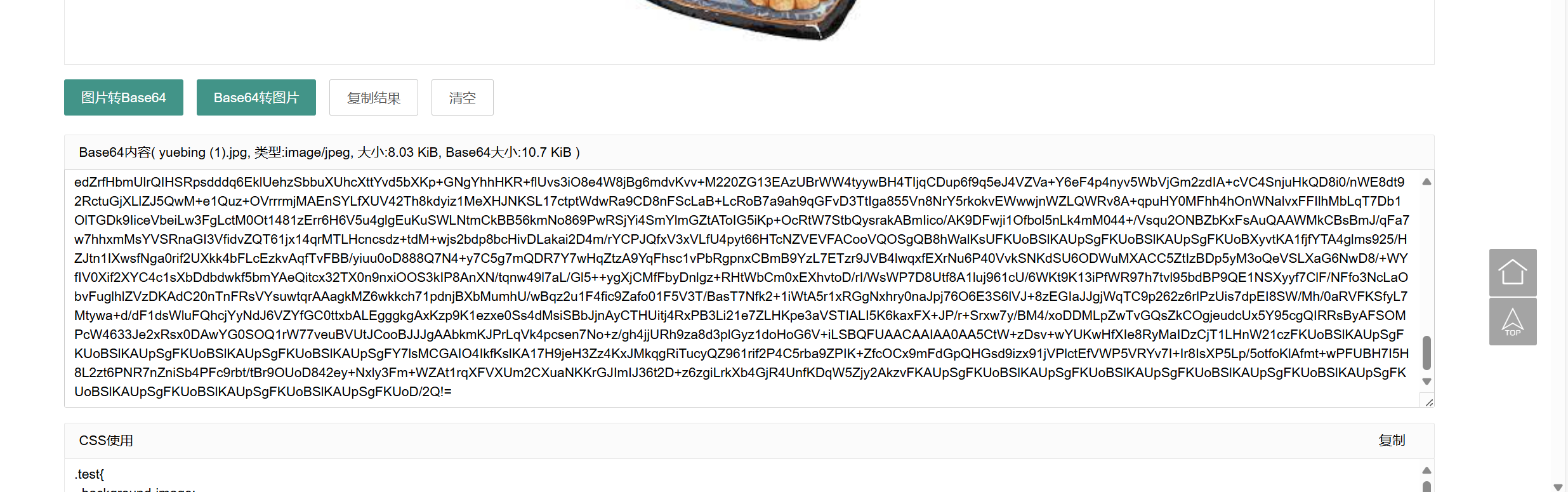
解压后得到jpg图片,在图片的尾部发现一串base64编码
List of file signatures
exp:
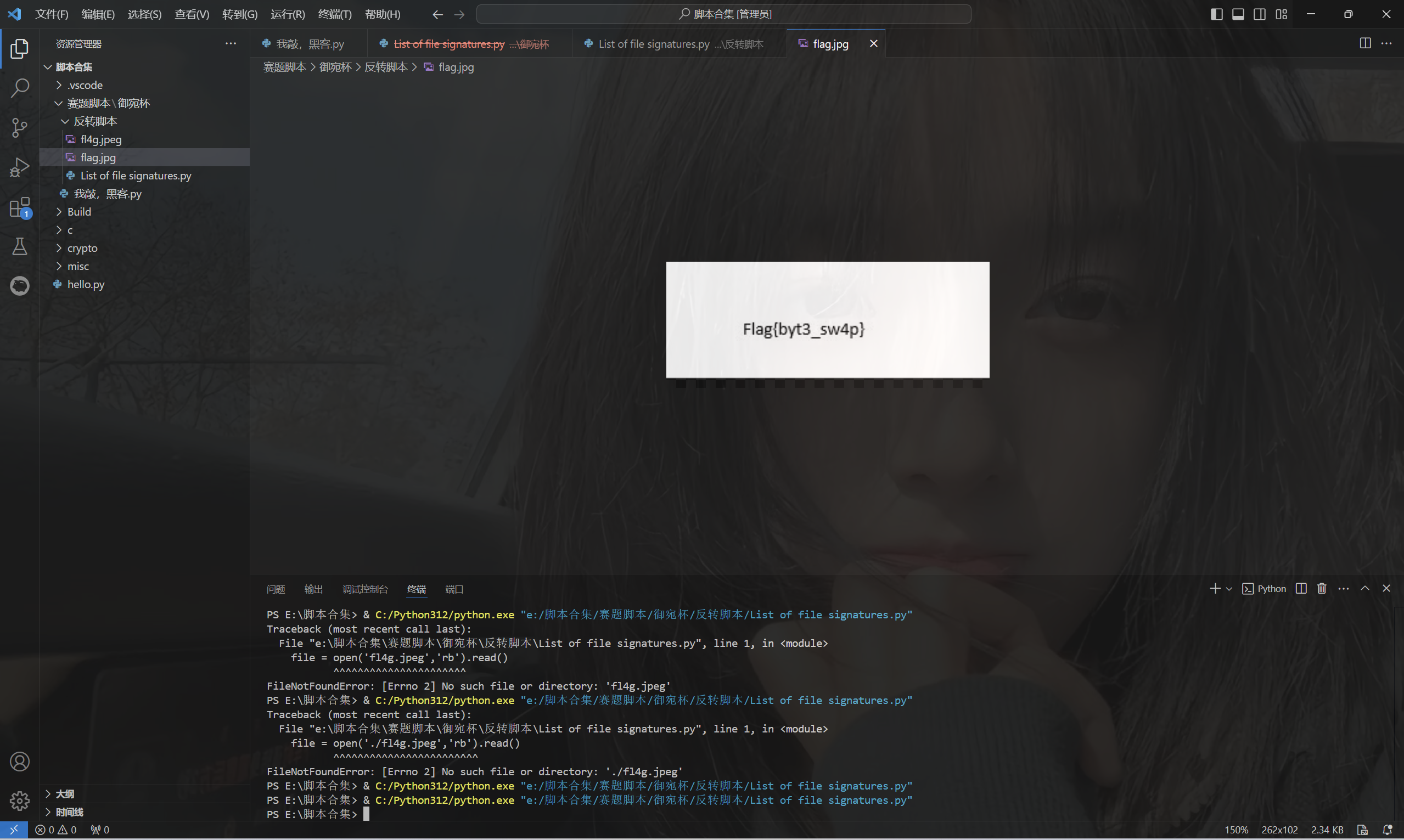
1 2 3 4 5 file = open('fl4g.jpeg','rb').read() res = b'' for i in range(0,len(file),4): res += file[i:i+4][::-1] open('flag.jpg','wb').write(res)
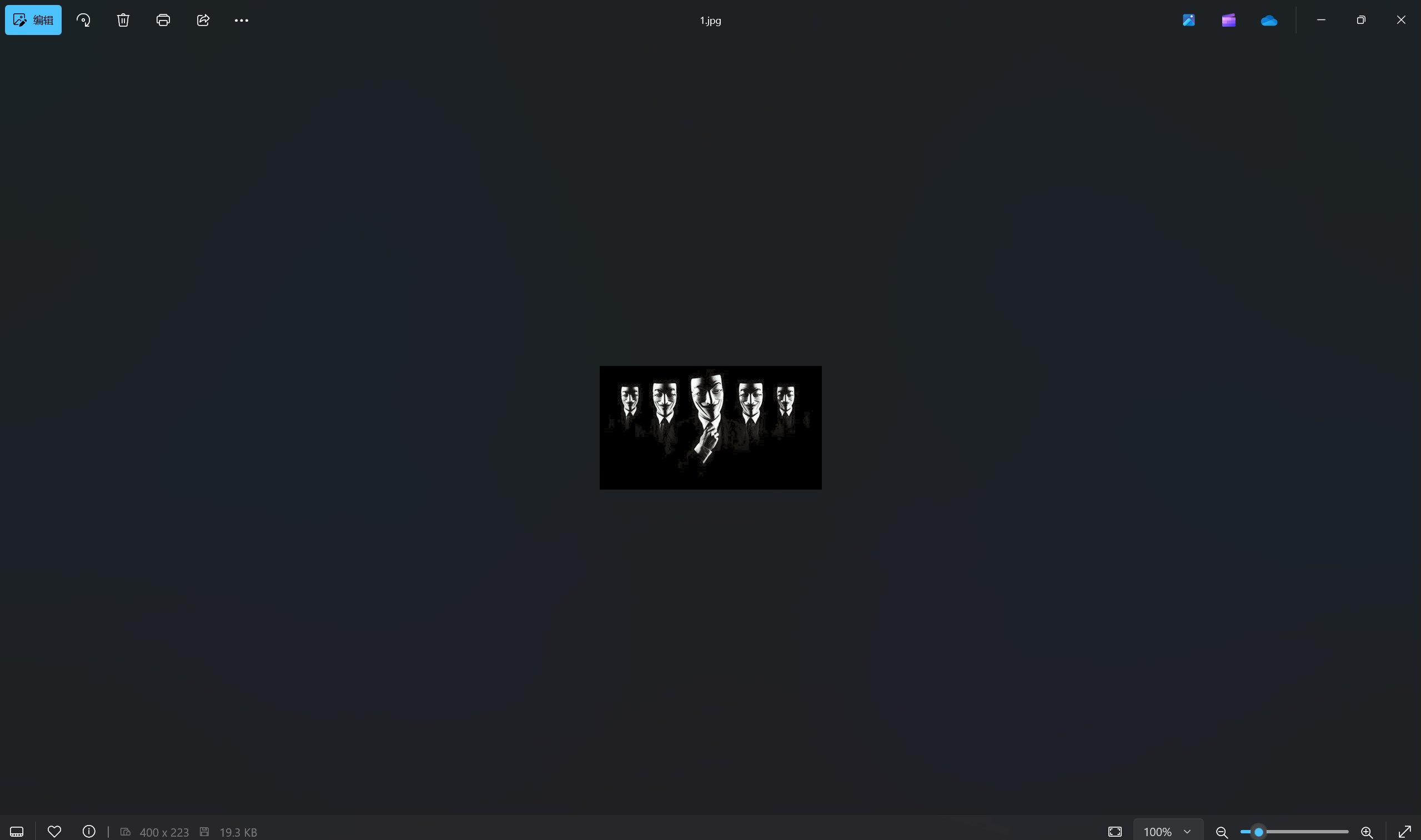
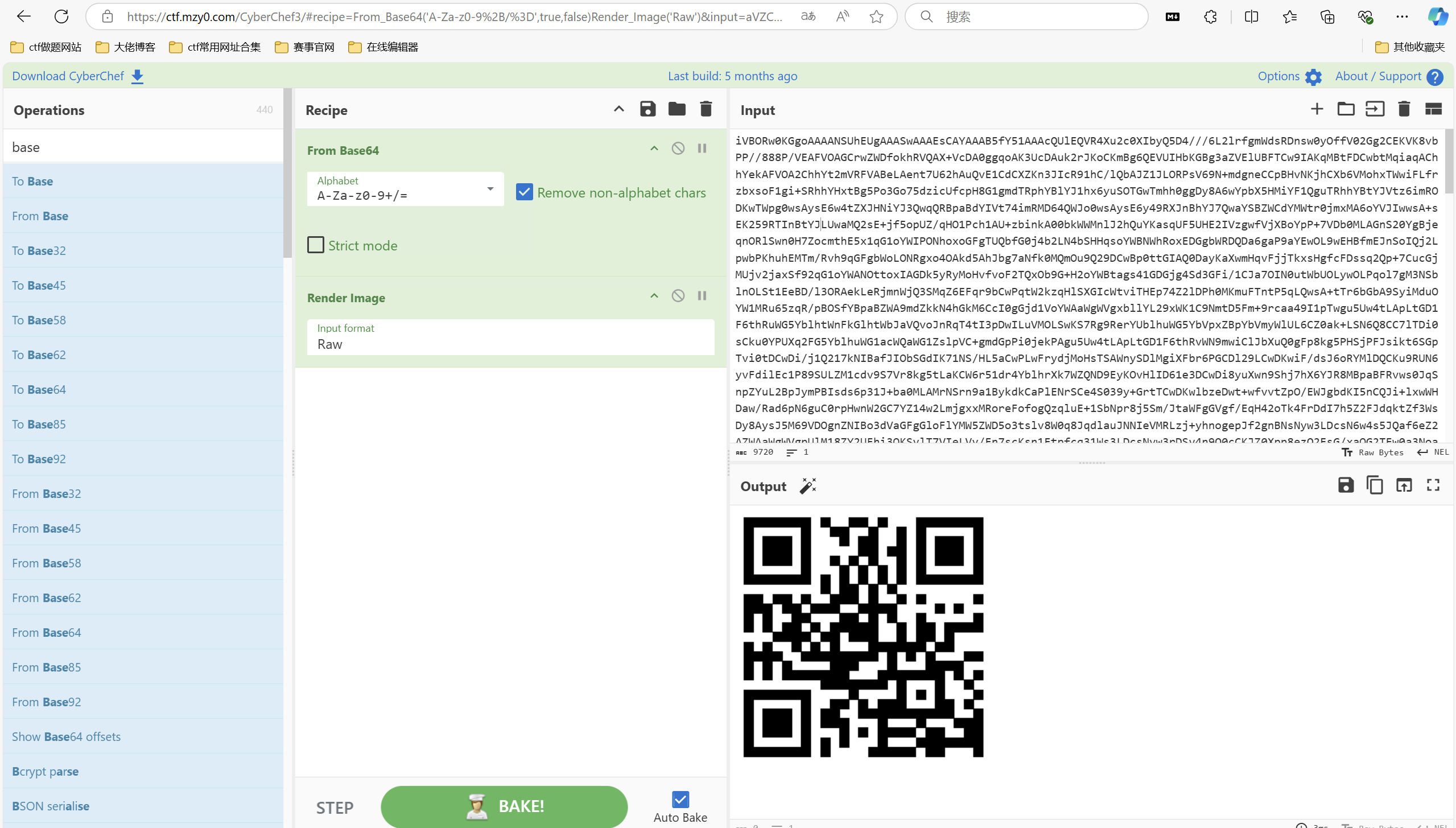
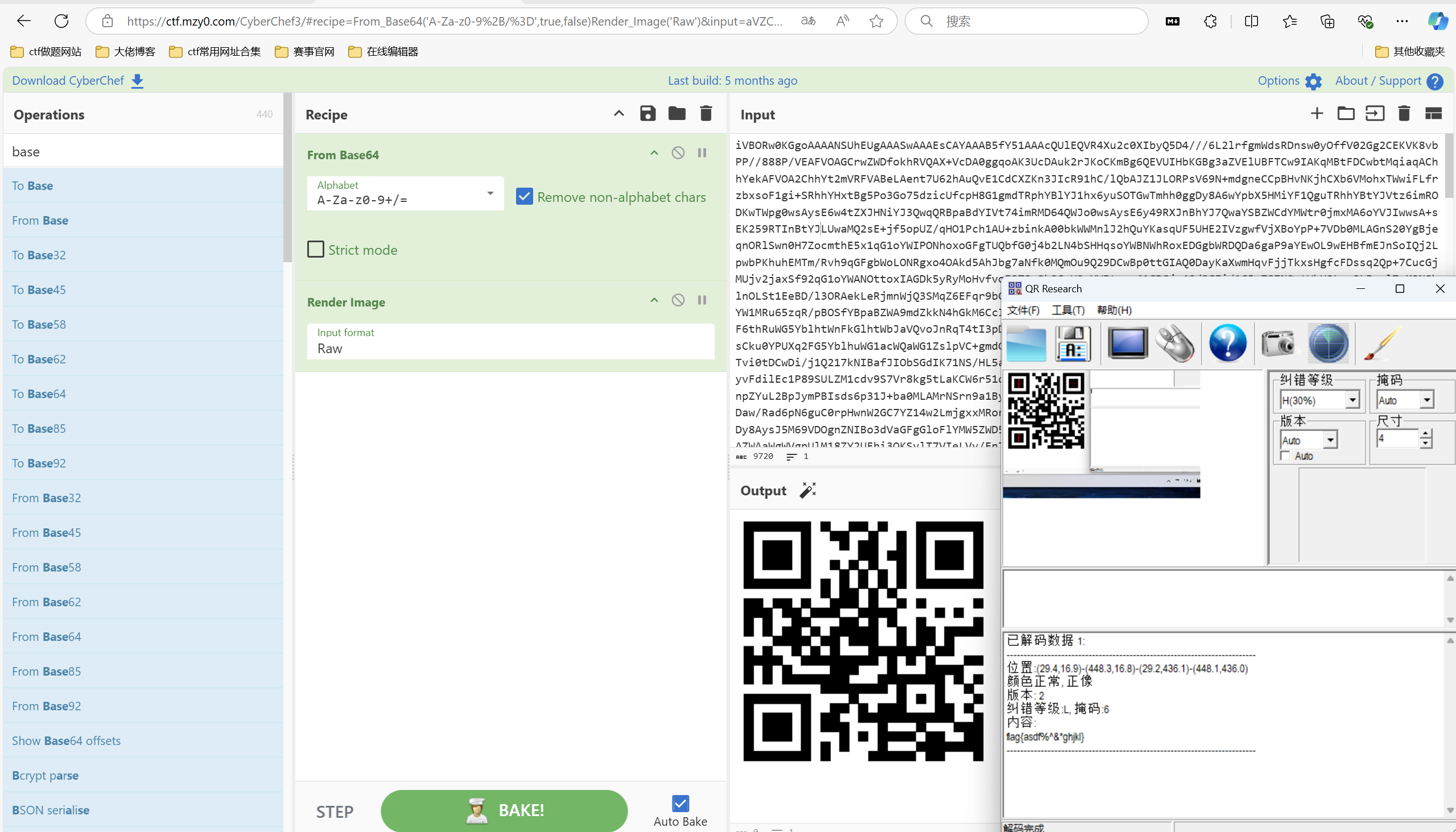
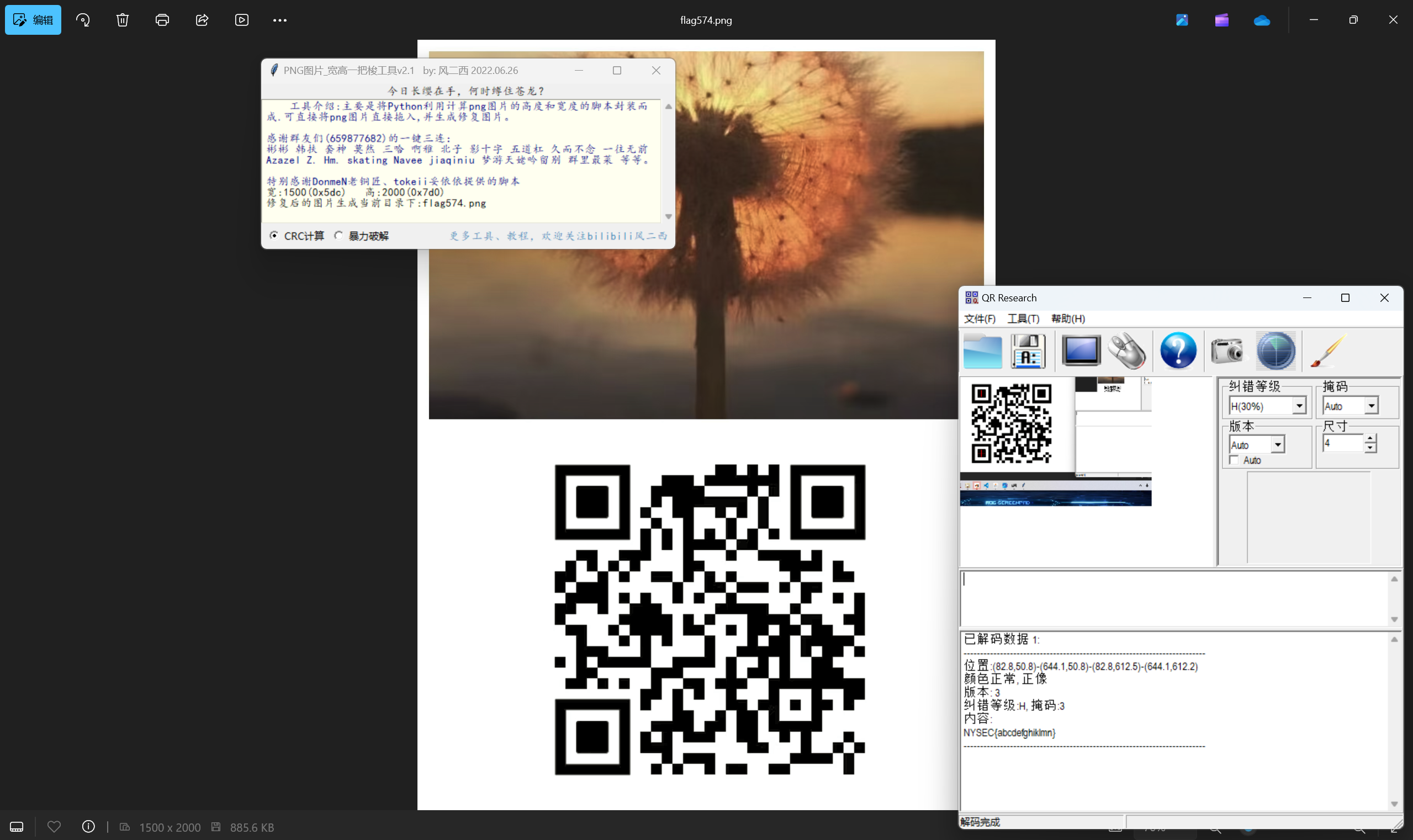
运行得到
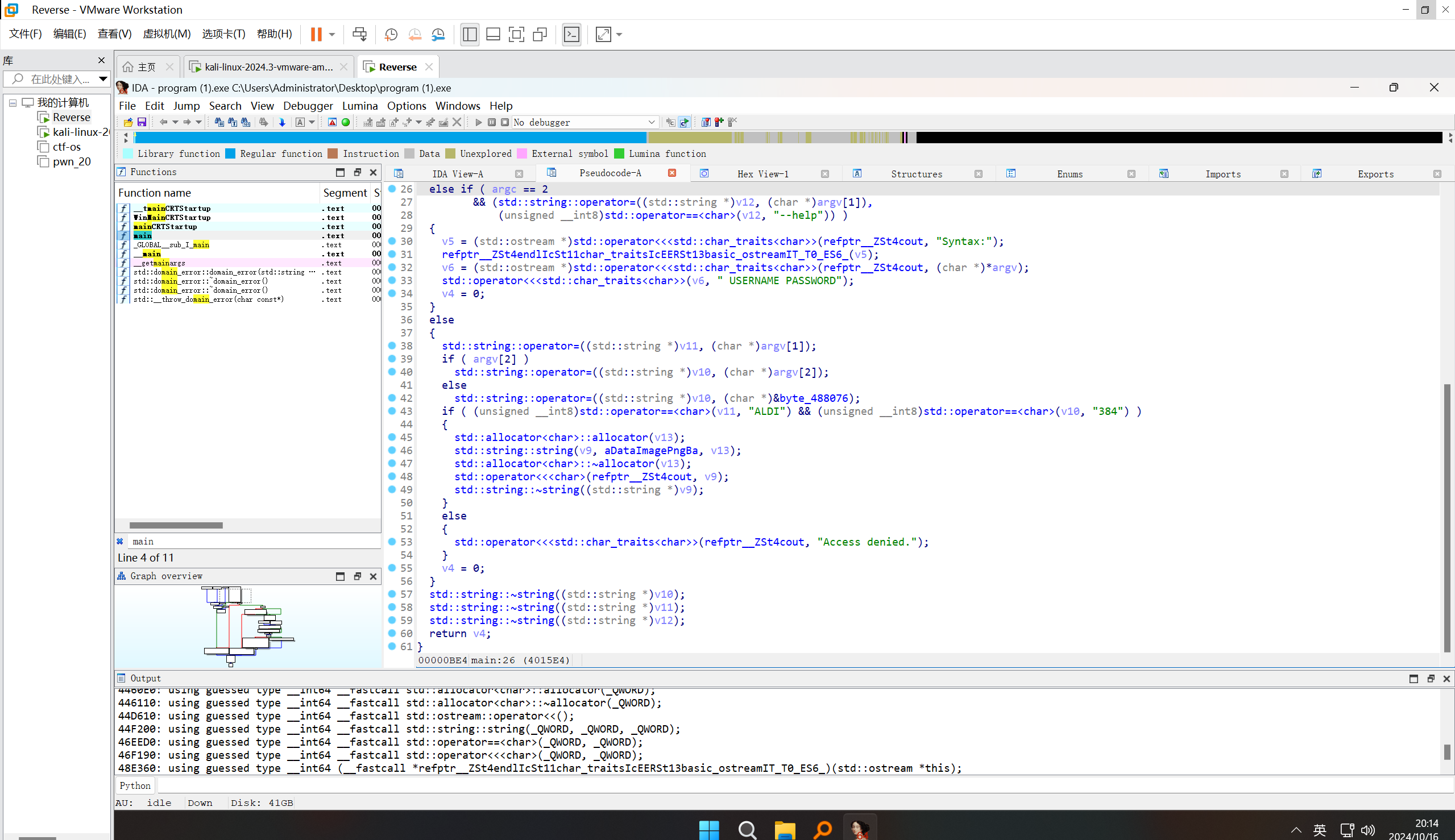
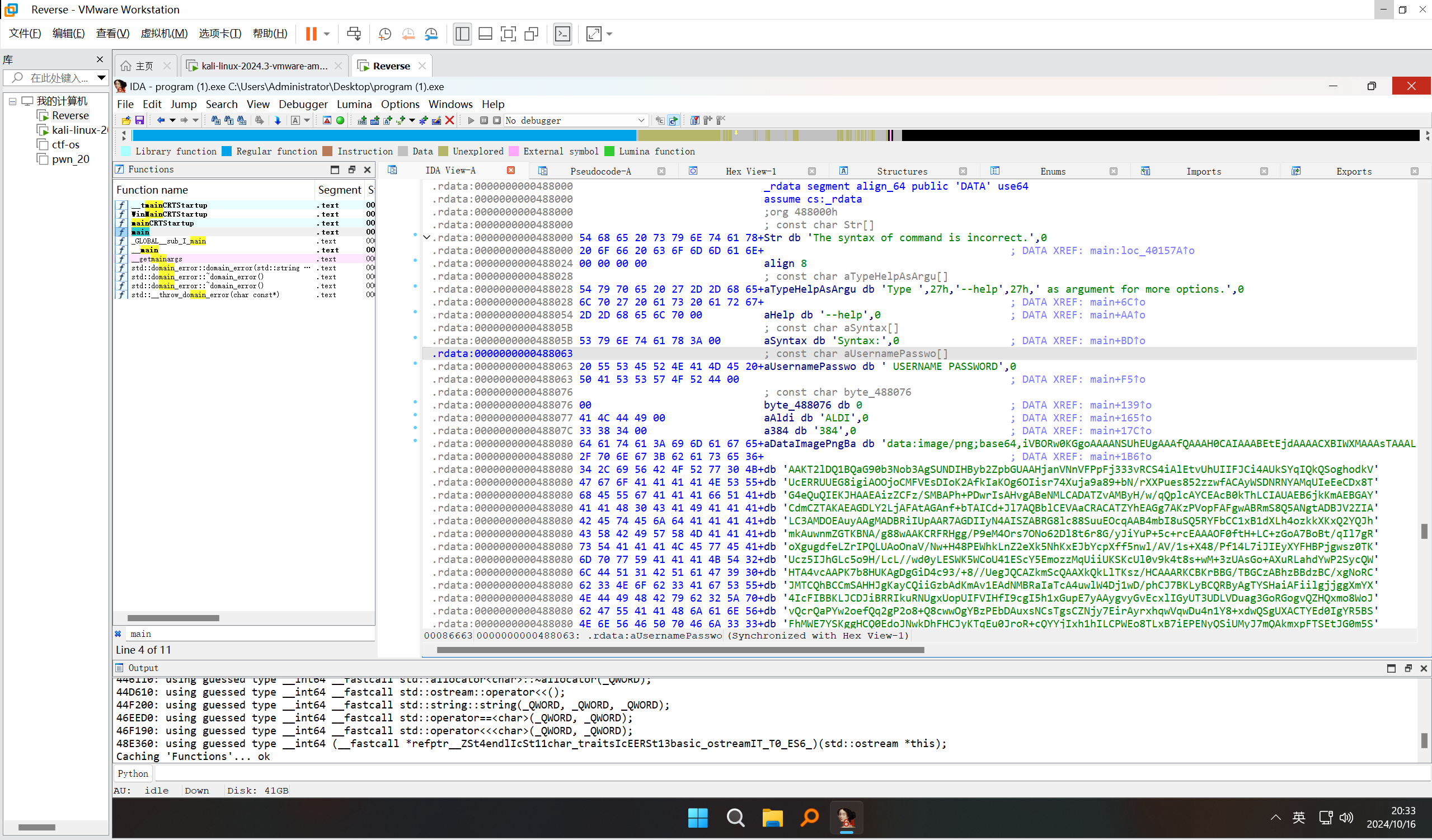
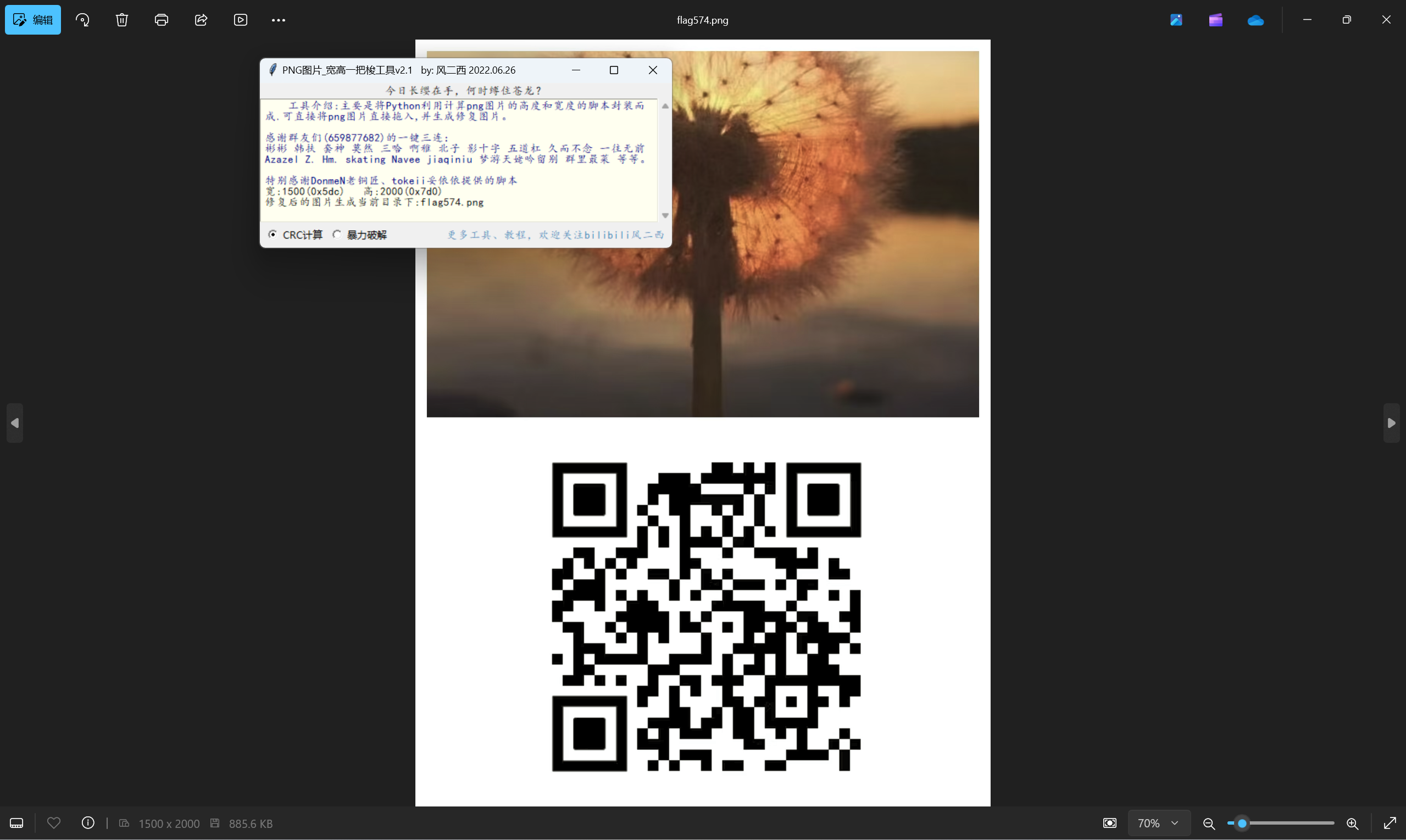
这能执行吗?
又是二维码捏
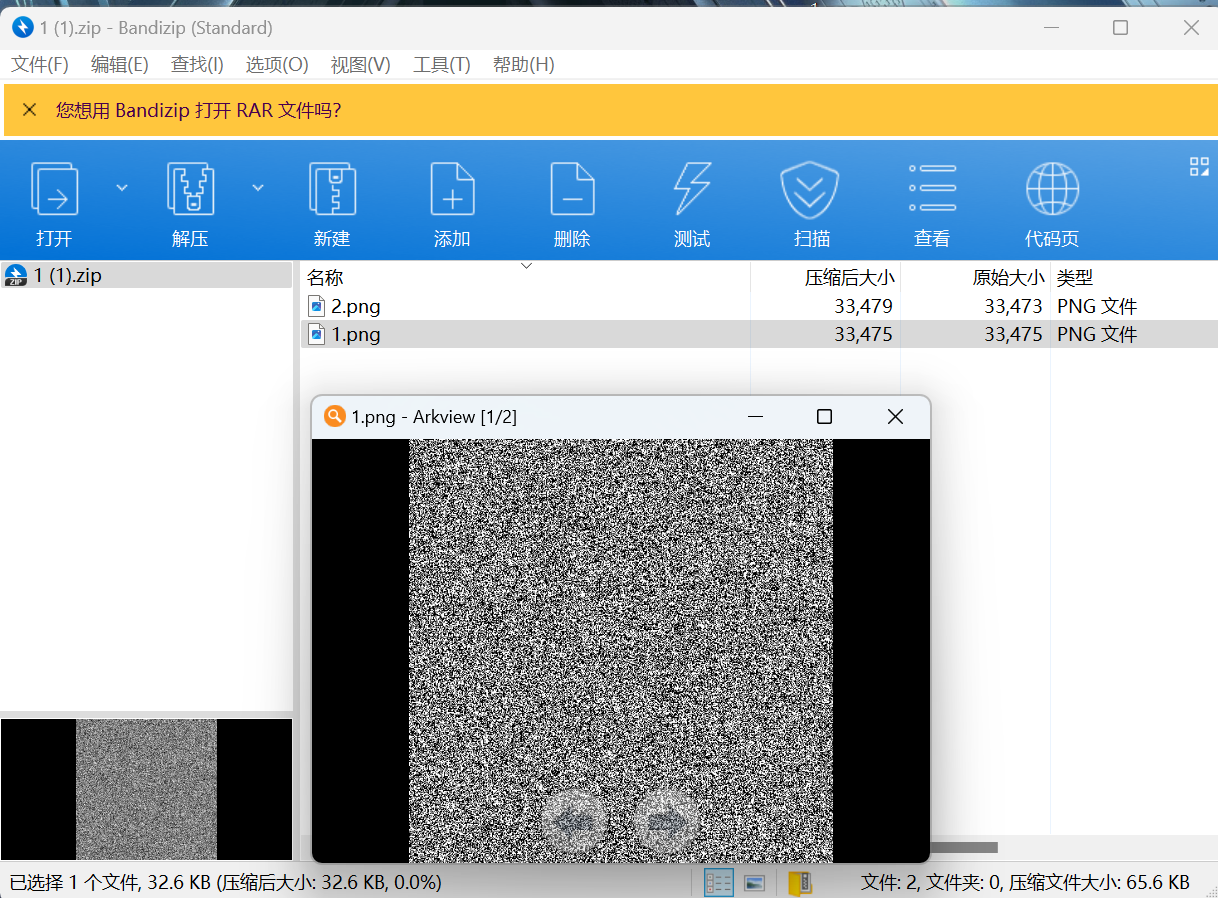
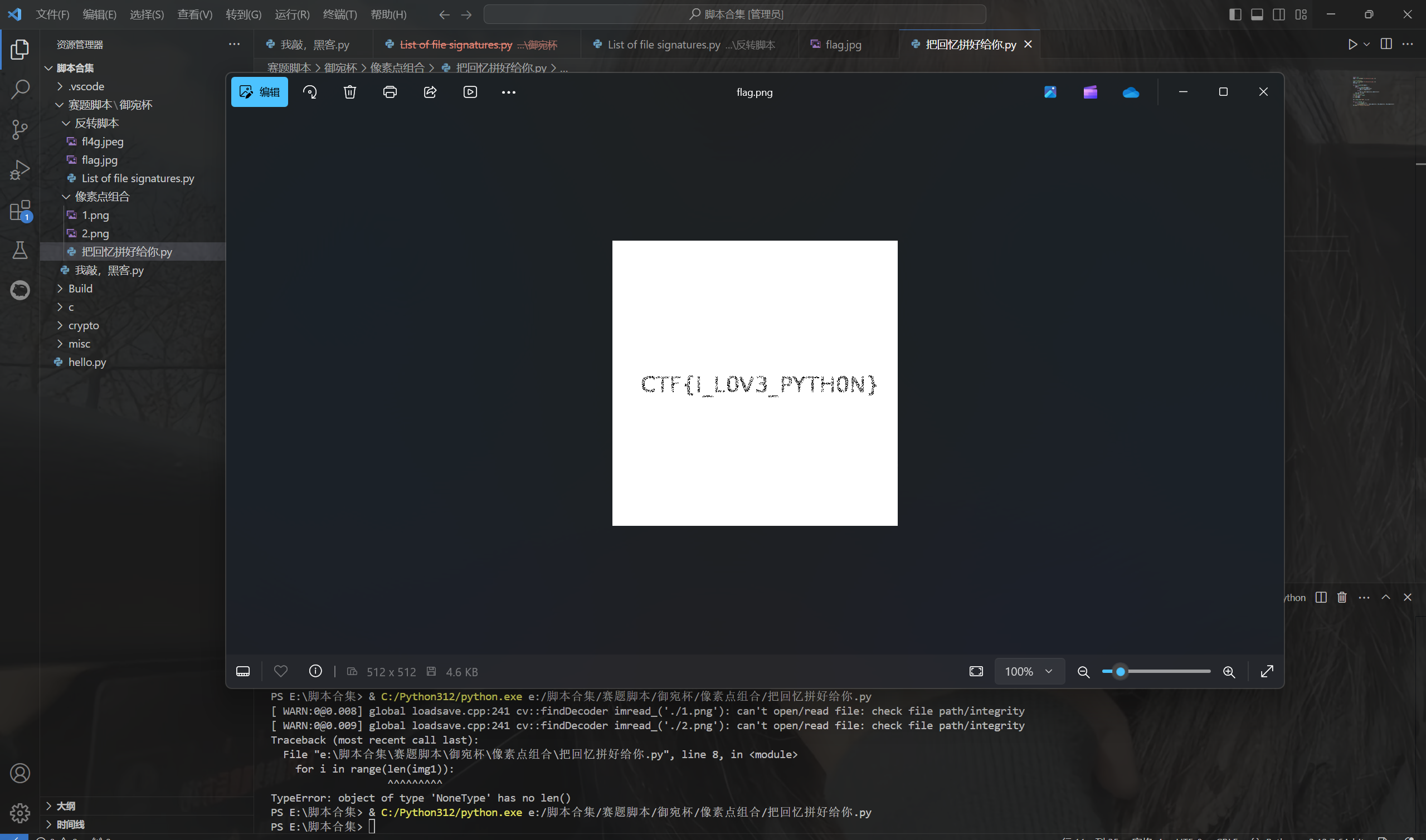
把回忆拼好给你
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 import cv2 img1 = cv2.imread(r'E:\\huiyi\\1.png',-1) # print(img1[2]) img2 = cv2.imread(r'E:\\huiyi\\2.png',-1) new_img = [] for i in range(len(img1)): img=[] for j in range(len(img1)): if img1[i][j]==img2[i][j]: img += [img1[i][j]] else: img += [max(img1[i][j],img2[i][j])] new_img += [img] # print(new_img) from PIL import Image x = len(img1) y = len(img1) im = Image.new("RGB", (x, y)) for i in range(0, x): for j in range(0, y): im.putpixel((i, j), (new_img[j][i], new_img[j][i], new_img[j][i])) im.save("E:\\huiyi\\flag.png")
运行得到
python?re?哦耶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 import base64 as rtfd import webbrowser import time def mikeSwift(cre): sto = [] gre = "" for i in cre: sto.append(i+str(len(i))) sto.append("h4ck" + i) for i in sto: gre+=i return gre def prompt(): return bytes(input("Welcome to the loading dock. What is the password?\t"), 'utf-8') def obfuscate(bys): fusc = rtfd.b64encode(bys) fusc += b"534345fdfgfgfdhty6y56yjl" fusc = str(fusc) fusc = fusc[2:len(fusc)-1] refus = [] for i in fusc: refus.append((str(i))) fusc="florSFIUEfet4565477" for i in refus: fusc+=i return fusc def crypt(sor): sro = [] fusc = "893" for i in range(len(sor)): sro.append(sor[i]+str(i)) sro.reverse() for i in sro: fusc+=i return fusc def grant(): print("Congartulation. Pleas Procid") webbrowser.open("https://ctflearn.com/index.php?action=find_problem_details&problem_id=449") def punish(): print("This is going to hurt.") while True: time.sleep(.1) webbrowser.open("https://www.youtube.com/watch?v=O3asoGVHix8") def main(): sik1 = prompt() sik = obfuscate(sik1) sik = crypt(sik) sik = mikeSwift(sik) if sik == "81h4ck891h4ck931h4ck3l1h4ckl81h4ck821h4ck2j1h4ckj81h4ck811h4ck1y1h4cky81h4ck801h4ck061h4ck671h4ck791h4ck951h4ck571h4ck781h4ck8y1h4cky71h4ck771h4ck761h4ck671h4ck761h4ck6y1h4cky71h4ck751h4ck5t1h4ckt71h4ck741h4ck4h1h4ckh71h4ck731h4ck3d1h4ckd71h4ck721h4ck2f1h4ckf71h4ck711h4ck1g1h4ckg71h4ck701h4ck0f1h4ckf61h4ck691h4ck9g1h4ckg61h4ck681h4ck8f1h4ckf61h4ck671h4ck7d1h4ckd61h4ck661h4ck6f1h4ckf61h4ck651h4ck551h4ck561h4ck641h4ck441h4ck461h4ck631h4ck331h4ck361h4ck621h4ck241h4ck461h4ck611h4ck131h4ck361h4ck601h4ck051h4ck551h4ck591h4ck9=1h4ck=51h4ck581h4ck801h4ck051h4ck571h4ck7n1h4ckn51h4ck561h4ck6R1h4ckR51h4ck551h4ck5s1h4cks51h4ck541h4ck4R1h4ckR51h4ck531h4ck3z1h4ckz51h4ck521h4ck2Z1h4ckZ51h4ck511h4ck1f1h4ckf51h4ck501h4ck0V1h4ckV41h4ck491h4ck9T1h4ckT41h4ck481h4ck8M1h4ckM41h4ck471h4ck7f1h4ckf41h4ck461h4ck6N1h4ckN41h4ck451h4ck5H1h4ckH41h4ck441h4ck4Z1h4ckZ41h4ck431h4ck3y1h4cky41h4ck421h4ck2R1h4ckR41h4ck411h4ck1z1h4ckz41h4ck401h4ck0d1h4ckd31h4ck391h4ck9r1h4ckr31h4ck381h4ck8N1h4ckN31h4ck371h4ck7G1h4ckG31h4ck361h4ck6N1h4ckN31h4ck351h4ck5i1h4cki31h4ck341h4ck491h4ck931h4ck331h4ck311h4ck131h4ck321h4ck2Z1h4ckZ31h4ck311h4ck101h4ck031h4ck301h4ck0w1h4ckw21h4ck291h4ck9m1h4ckm21h4ck281h4ck8R1h4ckR21h4ck271h4ck771h4ck721h4ck261h4ck6J1h4ckJ21h4ck251h4ck5X1h4ckX21h4ck241h4ck4Z1h4ckZ21h4ck231h4ck3i1h4cki21h4ck221h4ck2l1h4ckl21h4ck211h4ck131h4ck321h4ck201h4ck0Y1h4ckY11h4ck191h4ck971h4ck711h4ck181h4ck871h4ck711h4ck171h4ck741h4ck411h4ck161h4ck651h4ck511h4ck151h4ck561h4ck611h4ck141h4ck451h4ck511h4ck131h4ck341h4ck411h4ck121h4ck2t1h4ckt11h4ck111h4ck1e1h4cke11h4ck101h4ck0f1h4ckf91h4ck9E1h4ckE81h4ck8U1h4ckU71h4ck7I1h4ckI61h4ck6F1h4ckF51h4ck5S1h4ckS41h4ck4r1h4ckr31h4ck3o1h4cko21h4ck2l1h4ckl11h4ck1f1h4ckf01h4ck0": grant() else: punish() main()
整个程序的逻辑是:base64加密 –> 前后拼上垃圾字符 –> 将字符每一位和下标拼起来组成新字符串放 在一个数组中 –> 反转这个数组 –> 将所有字符串拼起来,并在首部添上 893 –> 将字符每一位和下标 拼起来,再拼上 h4ck 和这个字符,得到新字符串 按照程序逻辑逆就完事了
解密脚本
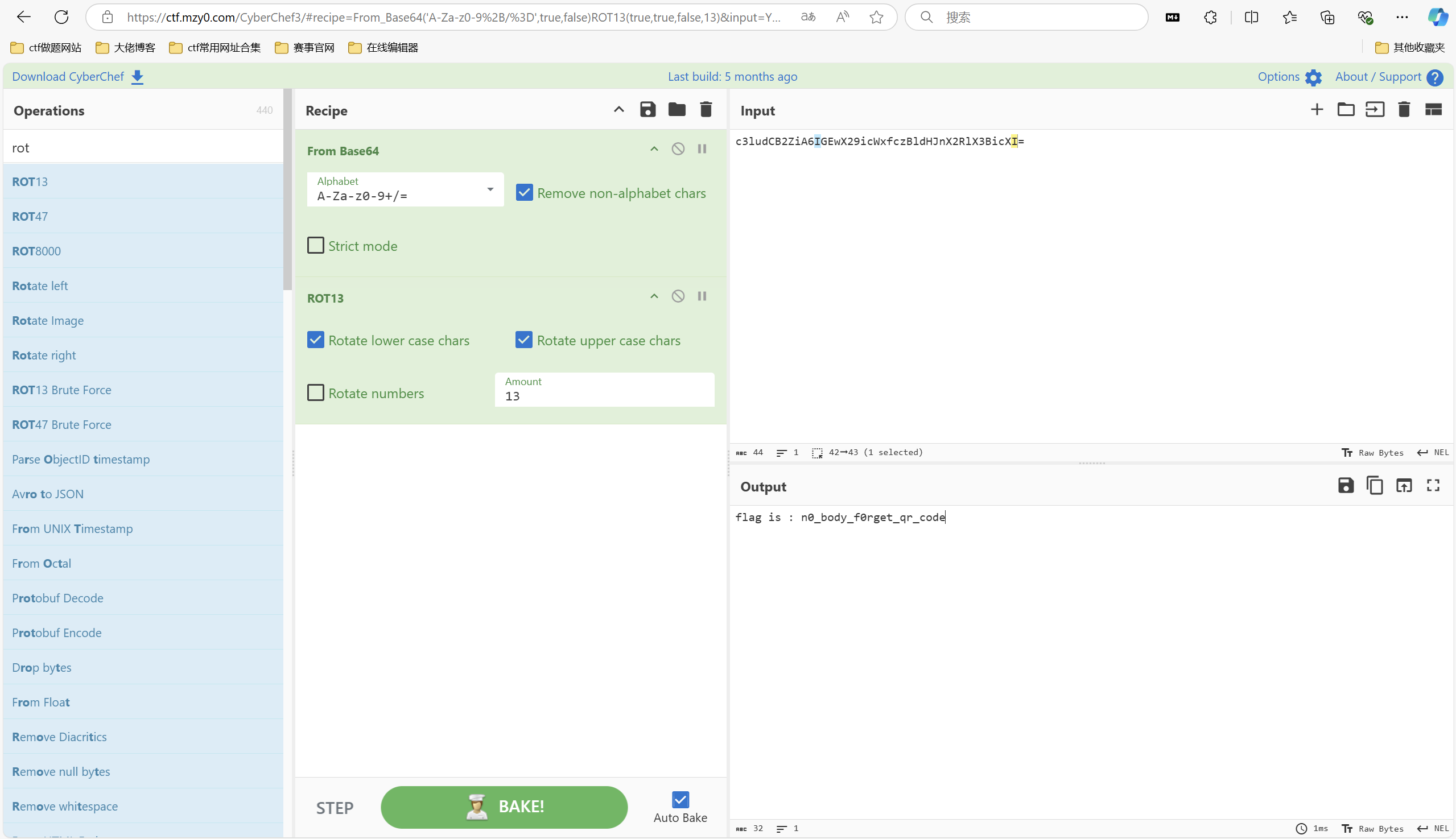
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 import base64 s="81h4ck891h4ck931h4ck3l1h4ckl81h4ck821h4ck2j1h4ckj81h4ck811h4ck1y1h4cky81h4ck801h4ck061h4ck671h4ck791h4ck951h4ck571h4ck781h4ck8y1h4cky71h4ck771h4ck761h4ck671h4ck761h4ck6y1h4cky71h4ck751h4ck5t1h4ckt71h4ck741h4ck4h1h4ckh71h4ck731h4ck3d1h4ckd71h4ck721h4ck2f1h4ckf71h4ck711h4ck1g1h4ckg71h4ck701h4ck0f1h4ckf61h4ck691h4ck9g1h4ckg61h4ck681h4ck8f1h4ckf61h4ck671h4ck7d1h4ckd61h4ck661h4ck6f1h4ckf61h4ck651h4ck551h4ck561h4ck641h4ck441h4ck461h4ck631h4ck331h4ck361h4ck621h4ck241h4ck461h4ck611h4ck131h4ck361h4ck601h4ck051h4ck551h4ck591h4ck9=1h4ck=51h4ck581h4ck801h4ck051h4ck571h4ck7n1h4ckn51h4ck561h4ck6R1h4ckR51h4ck551h4ck5s1h4cks51h4ck541h4ck4R1h4ckR51h4ck531h4ck3z1h4ckz51h4ck521h4ck2Z1h4ckZ51h4ck511h4ck1f1h4ckf51h4ck501h4ck0V1h4ckV41h4ck491h4ck9T1h4ckT41h4ck481h4ck8M1h4ckM41h4ck471h4ck7f1h4ckf41h4ck461h4ck6N1h4ckN41h4ck451h4ck5H1h4ckH41h4ck441h4ck4Z1h4ckZ41h4ck431h4ck3y1h4cky41h4ck421h4ck2R1h4ckR41h4ck411h4ck1z1h4ckz41h4ck401h4ck0d1h4ckd31h4ck391h4ck9r1h4ckr31h4ck381h4ck8N1h4ckN31h4ck371h4ck7G1h4ckG31h4ck361h4ck6N1h4ckN31h4ck351h4ck5i1h4cki31h4ck341h4ck491h4ck931h4ck331h4ck311h4ck131h4ck321h4ck2Z1h4ckZ31h4ck311h4ck101h4ck031h4ck301h4ck0w1h4ckw21h4ck291h4ck9m1h4ckm21h4ck281h4ck8R1h4ckR21h4ck271h4ck771h4ck721h4ck261h4ck6J1h4ckJ21h4ck251h4ck5X1h4ckX21h4ck241h4ck4Z1h4ckZ21h4ck231h4ck3i1h4cki21h4ck221h4ck2l1h4ckl21h4ck211h4ck131h4ck321h4ck201h4ck0Y1h4ckY11h4ck191h4ck971h4ck711h4ck181h4ck871h4ck711h4ck171h4ck741h4ck411h4ck161h4ck651h4ck511h4ck151h4ck561h4ck611h4ck141h4ck451h4ck511h4ck131h4ck341h4ck411h4ck121h4ck2t1h4ckt11h4ck111h4ck1e1h4cke11h4ck101h4ck0f1h4ckf91h4ck9E1h4ckE81h4ck8U1h4ckU71h4ck7I1h4ckI61h4ck6F1h4ckF51h4ck5S1h4ckS41h4ck4r1h4ckr31h4ck3o1h4cko21h4ck2l1h4ckl11h4ck1f1h4ckf01h4ck0" ss='' for i in range(0,len(s),7): ss+=s[i] tmp=ss[3:] sss='' for i in range(0,220,3): sss+=tmp[i] for i in range(221,len(tmp),2): sss+=tmp[i] sss=sss[::-1] print(base64.b64decode(sss[19:][:-24]))
运行得到
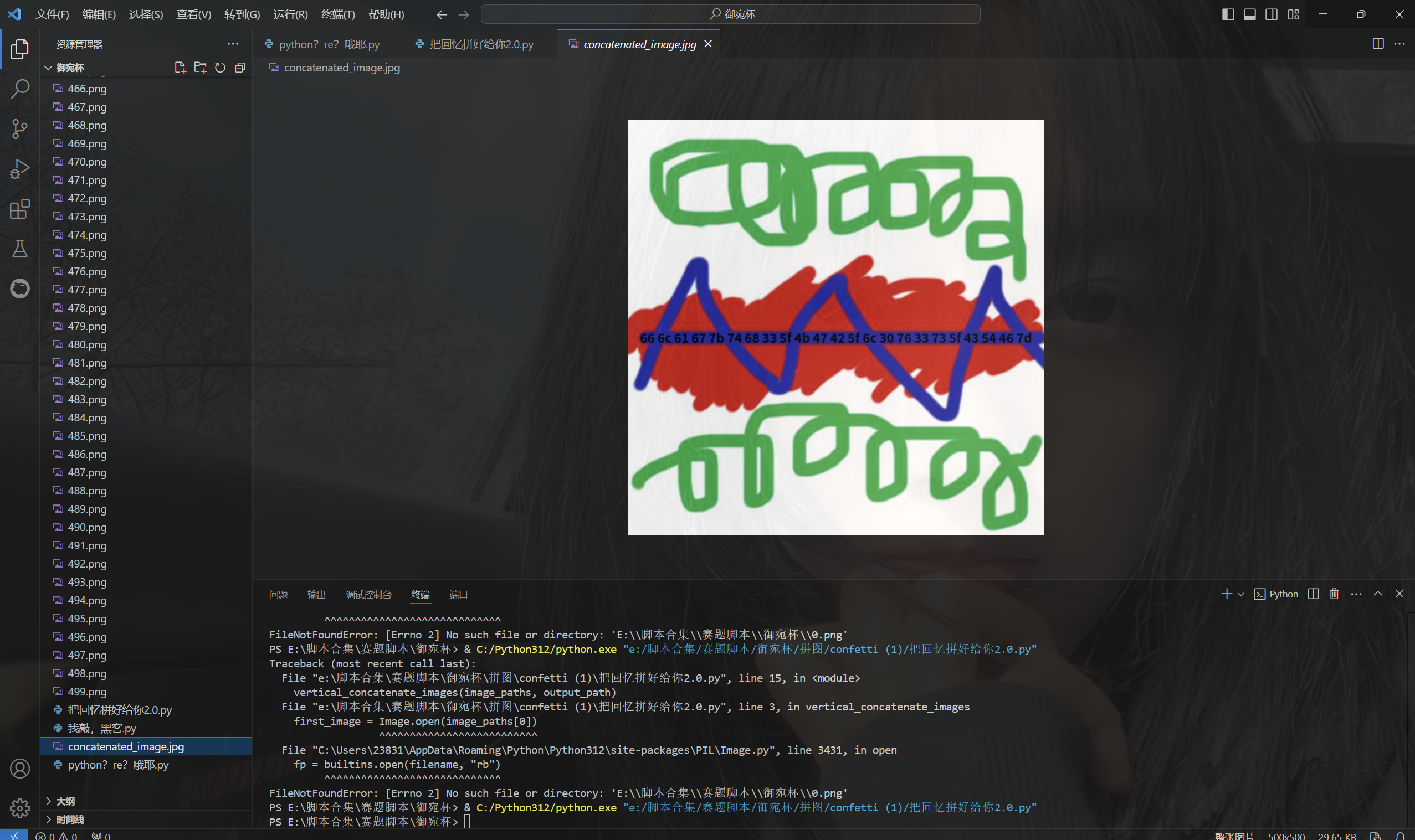
把回忆拼好给你2.0
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from PIL import Image def vertical_concatenate_images(image_paths, output_path): first_image = Image.open(image_paths[0]) width, height = first_image.size total_height = sum([Image.open(img).size[1] for img in image_paths]) concatenated_image = Image.new('RGB', (width, total_height)) y_offset = 0 for img_path in image_paths: img = Image.open(img_path) concatenated_image.paste(img, (0, y_offset)) y_offset += img.size[1] concatenated_image.save(output_path) image_paths = [f'{i}.png' for i in range(0, 500)] output_path = 'concatenated_image.jpg' vertical_concatenate_images(image_paths, output_path)
运行得到
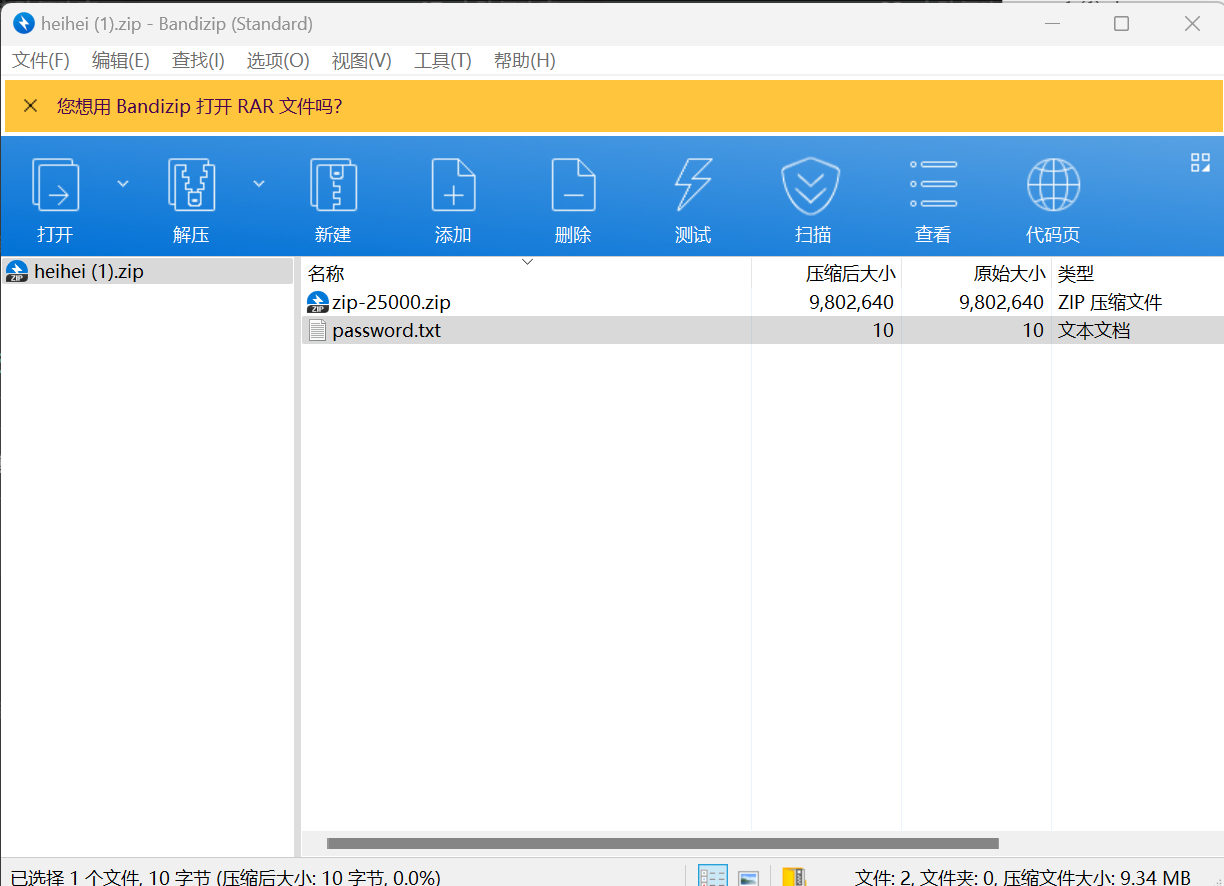
不会真有人一个一个解压缩吧?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 import os import shutil def unzip(zipname,pwd,filePath2): print(zipname,pwd,filePath2) os.system(f'unzip -P {pwd} {zipname} -d {filePath2}') cnt = 0 while True: filePath1 = './'+str(cnt) + '/' cnt = (cnt + 1) & 1 filePath2 = './'+str(cnt) + '/' for i,j,k in os.walk(filePath1): pwd = '' if 'password.txt' in k: pwd = open(filePath1 + 'password.txt','r').read().strip() # print(pwd) else: break for i in k: if '.zip' in i: # print(i,pwd,filePath2) shutil.rmtree(filePath2) os.mkdir(filePath2) unzip(filePath1+i,pwd,filePath2)
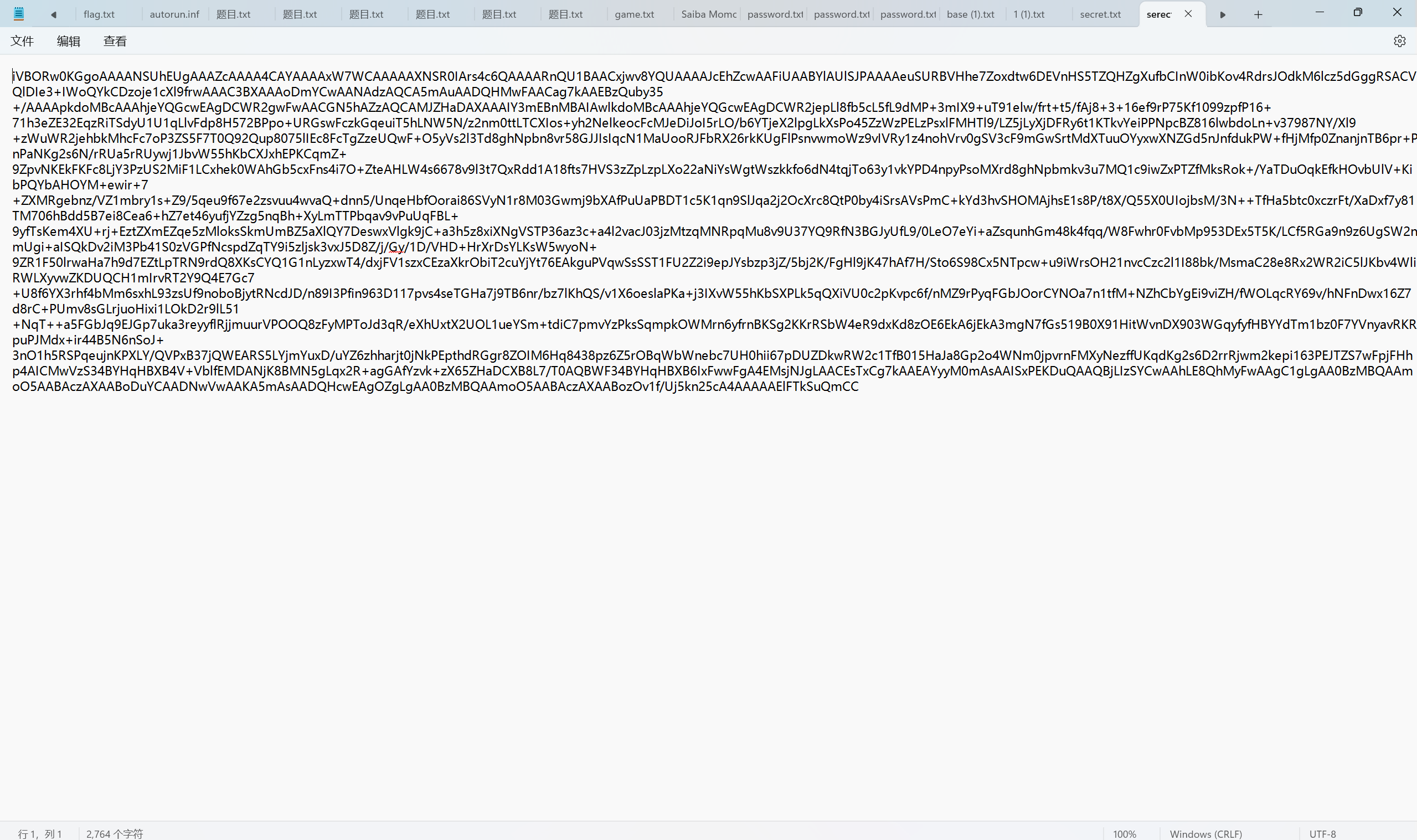
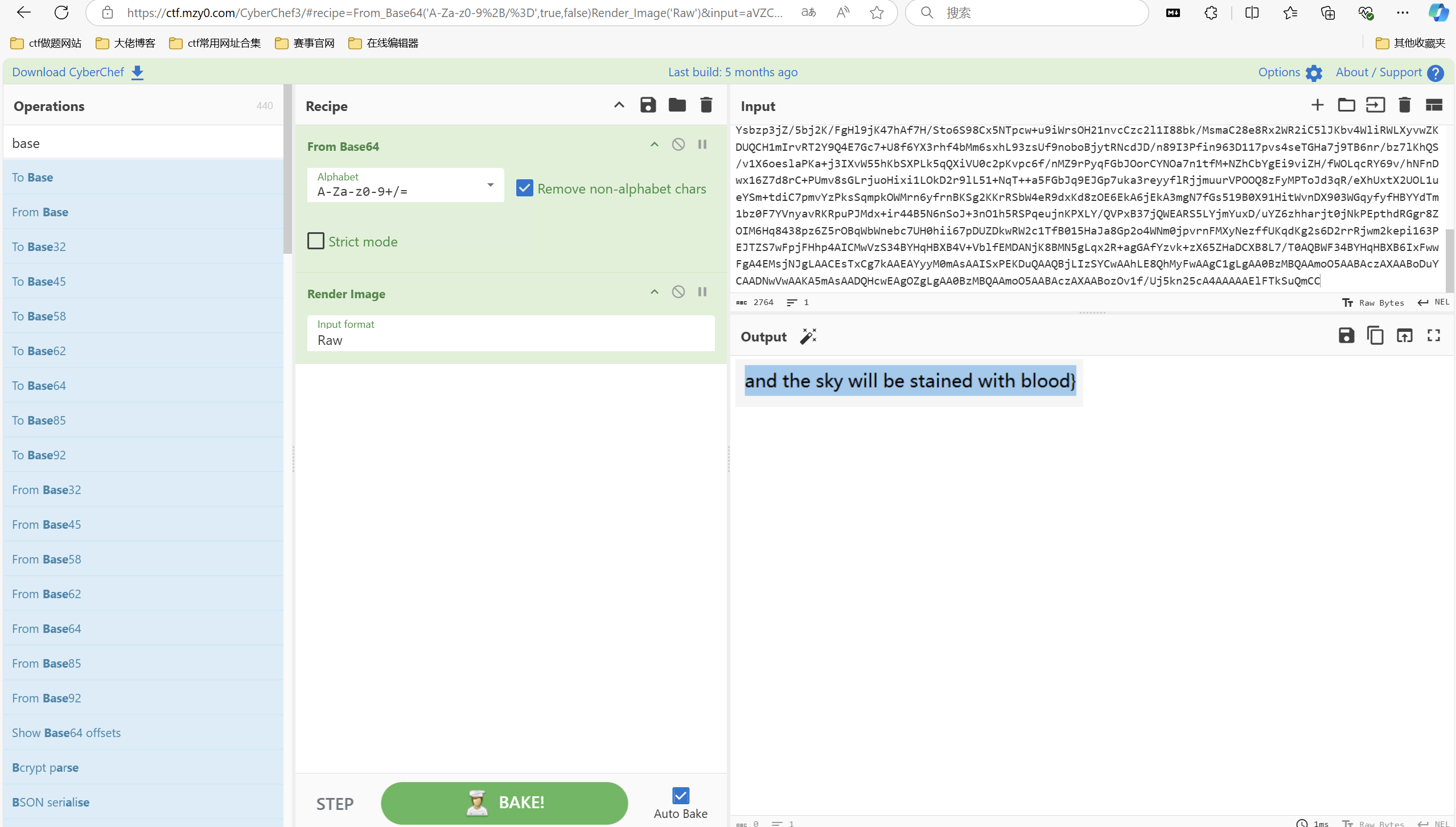
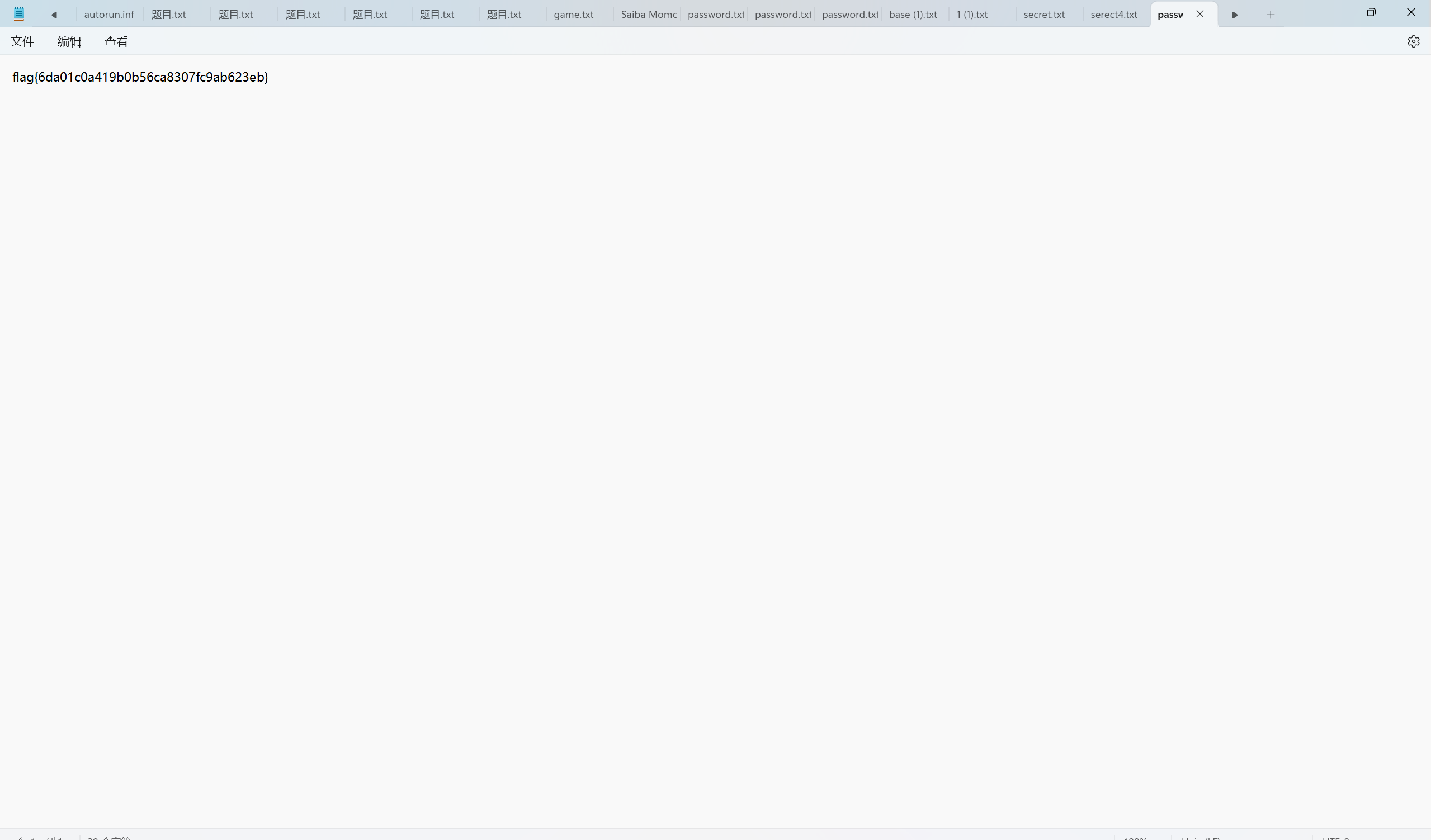
最后flag为flag{1_TH1NK_U_G00D_4T_SCR1PT1N9_botanbell_1s_h3r3^_^}
来签个到吧,包简单的
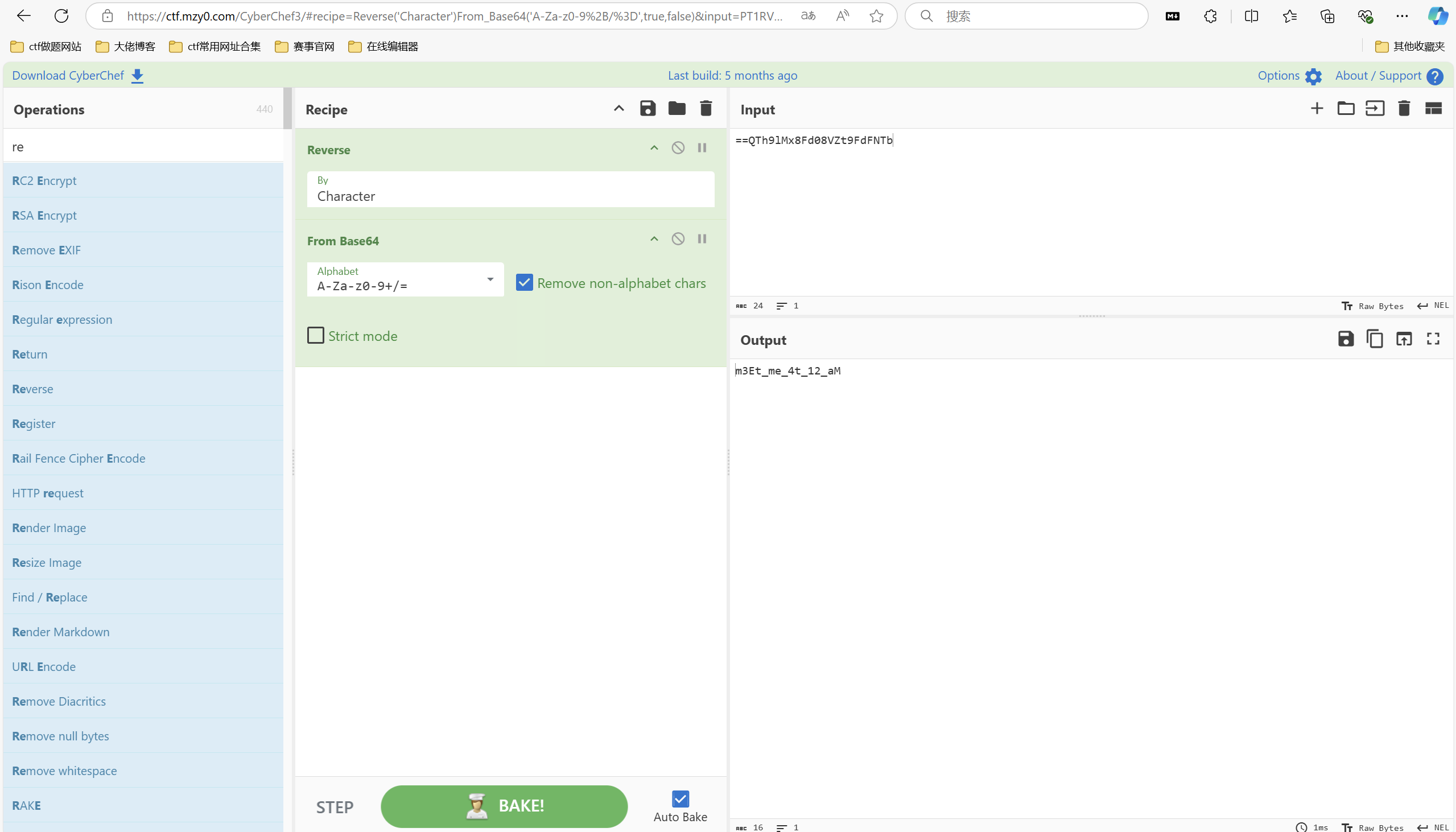
中秋特辑(1) 把base64后面的== 改为 !=
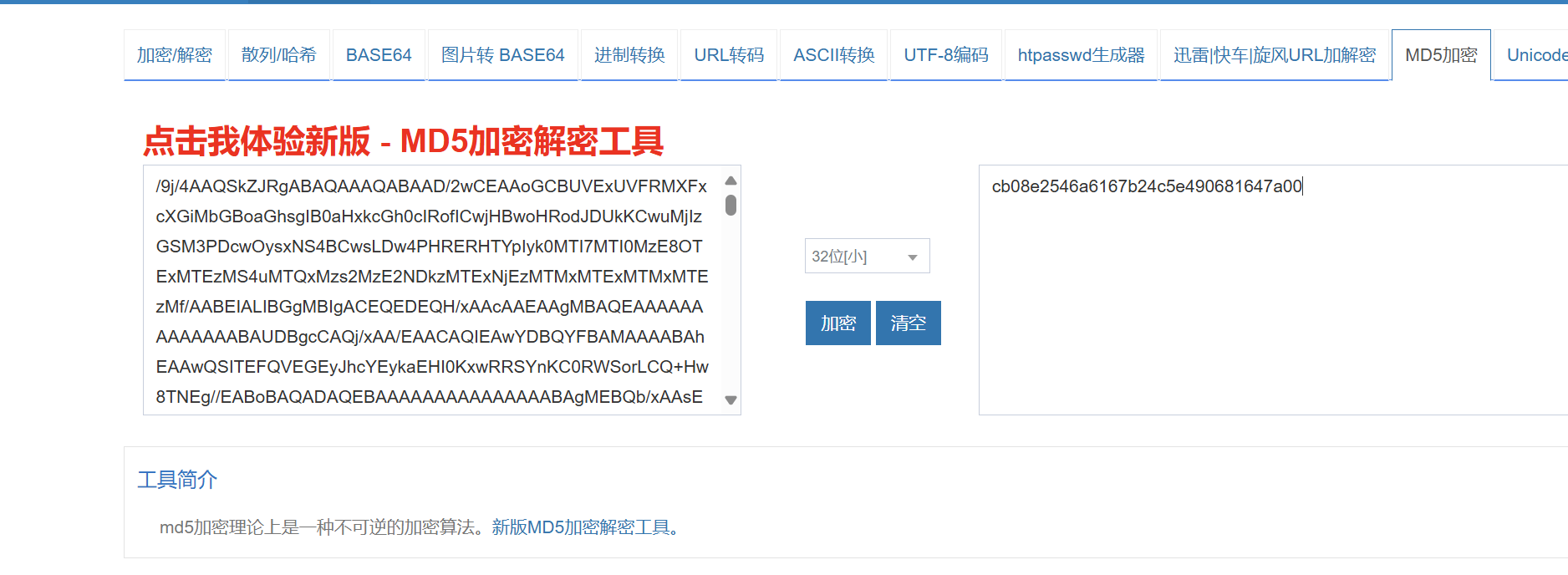
md5加密
这是?配置文件?
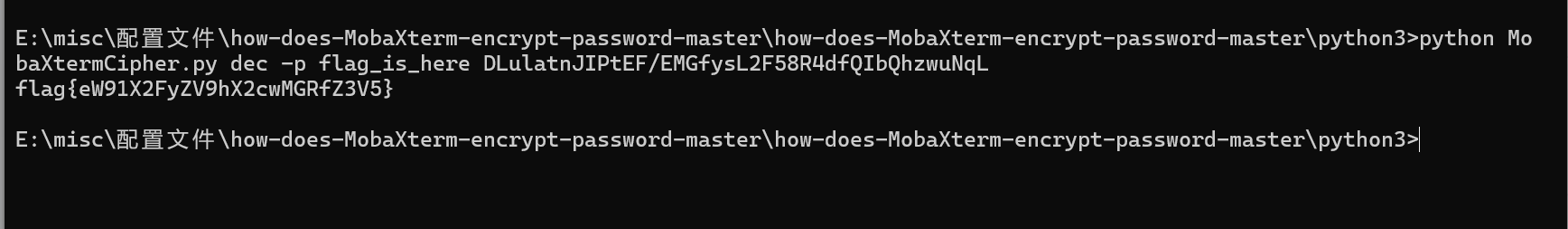
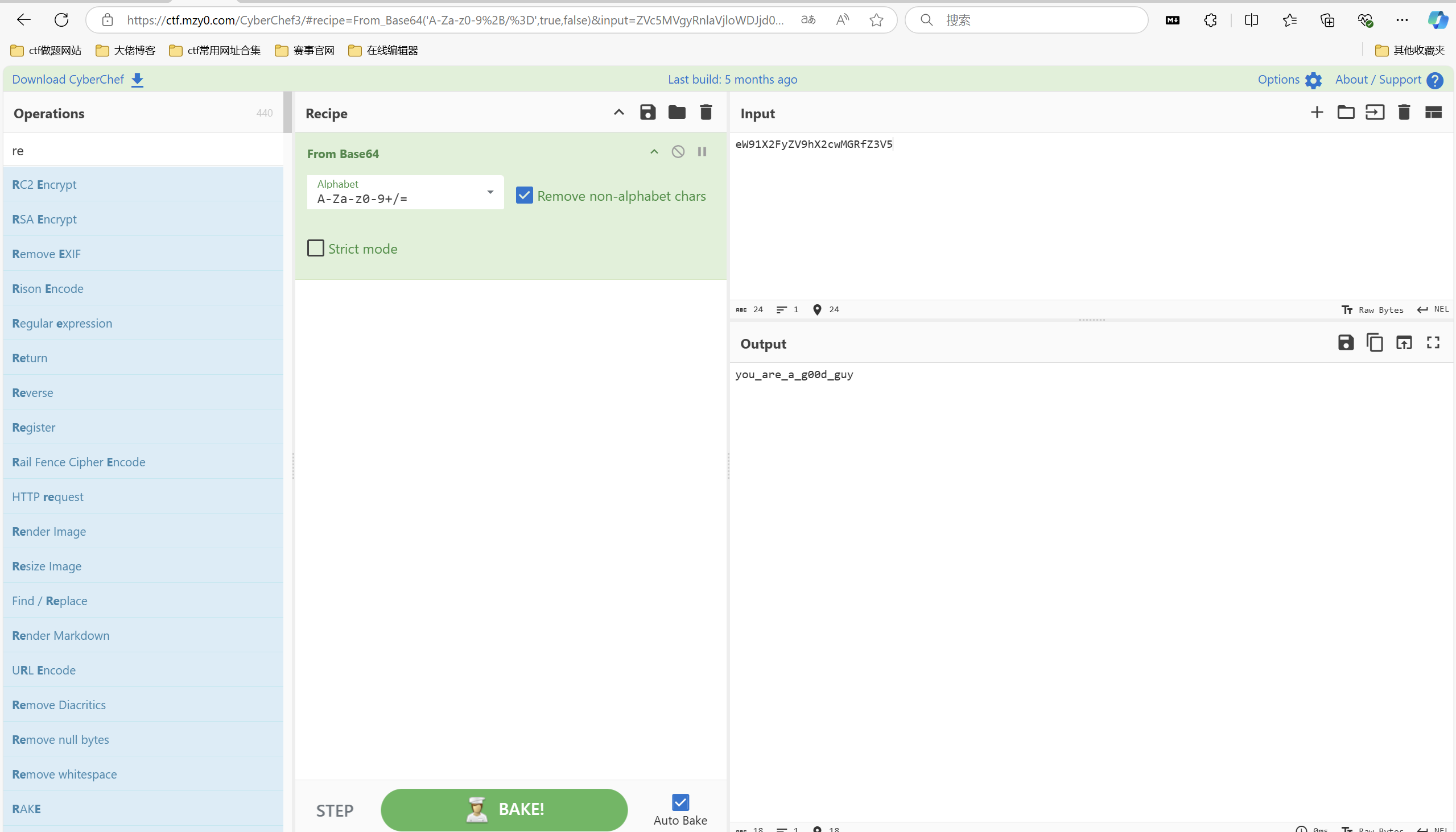
python MobaXtermCipher.py dec -p flag_is_here DLulatnJIPtEF/EMGfysL2F58R4dfQIbQhzwuNqL
base解密
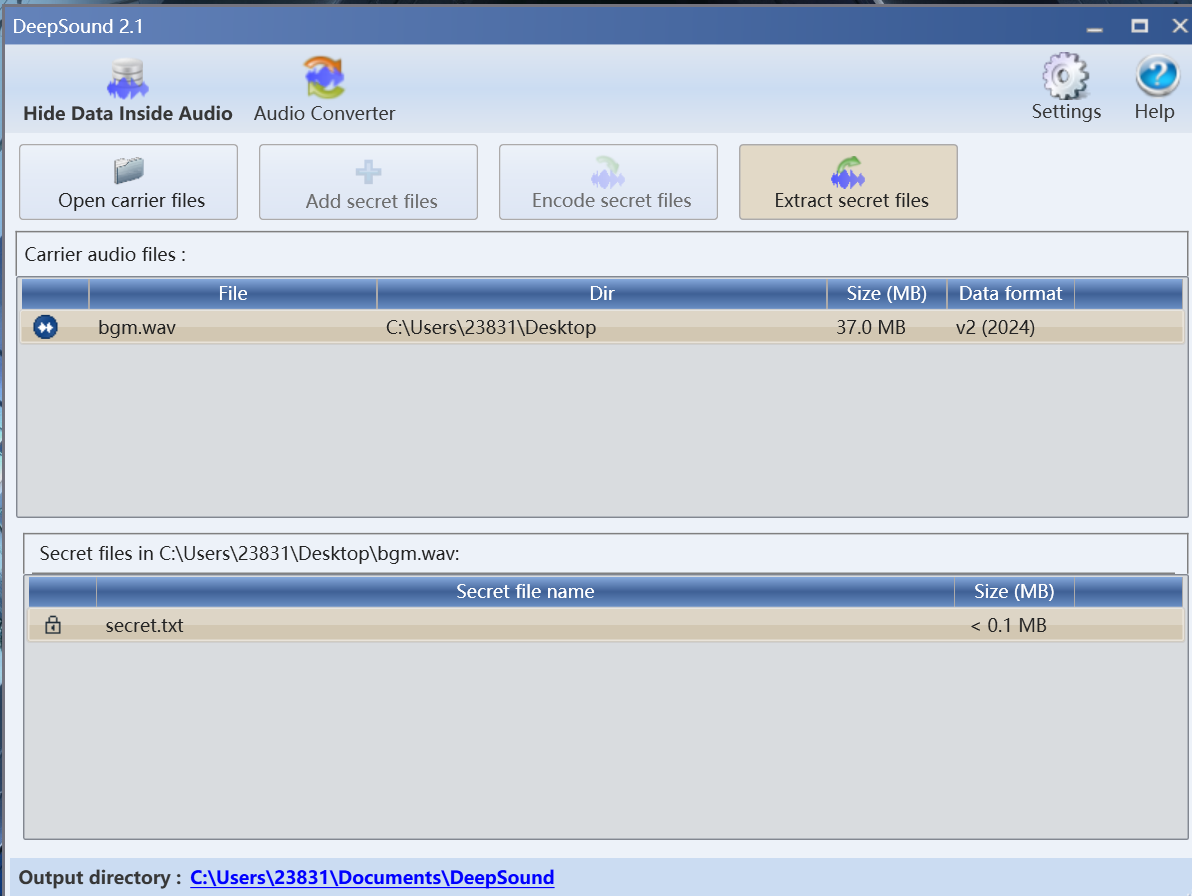
图片的隐藏
下载附件
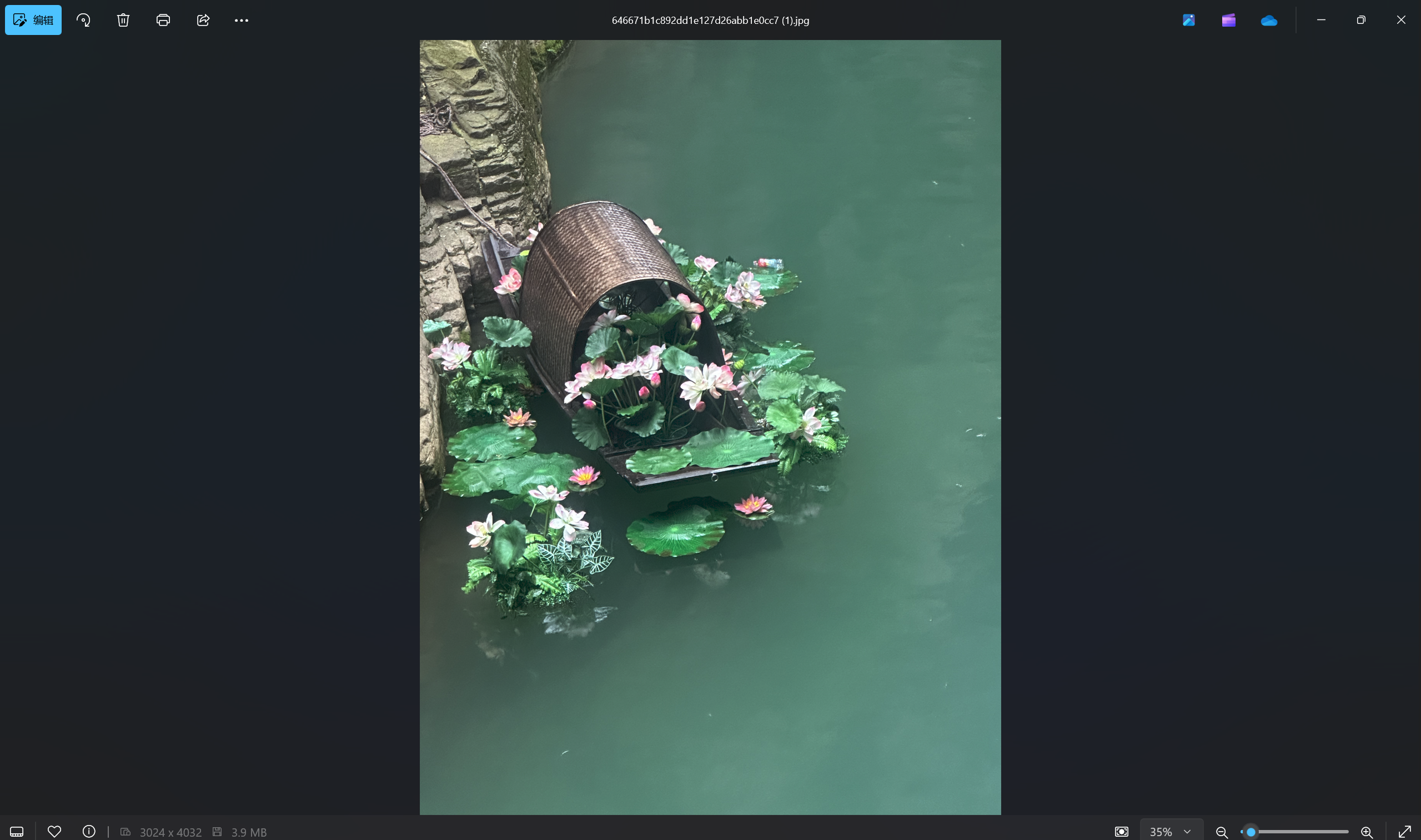
快来社我_1
下载附件
快来社我_2
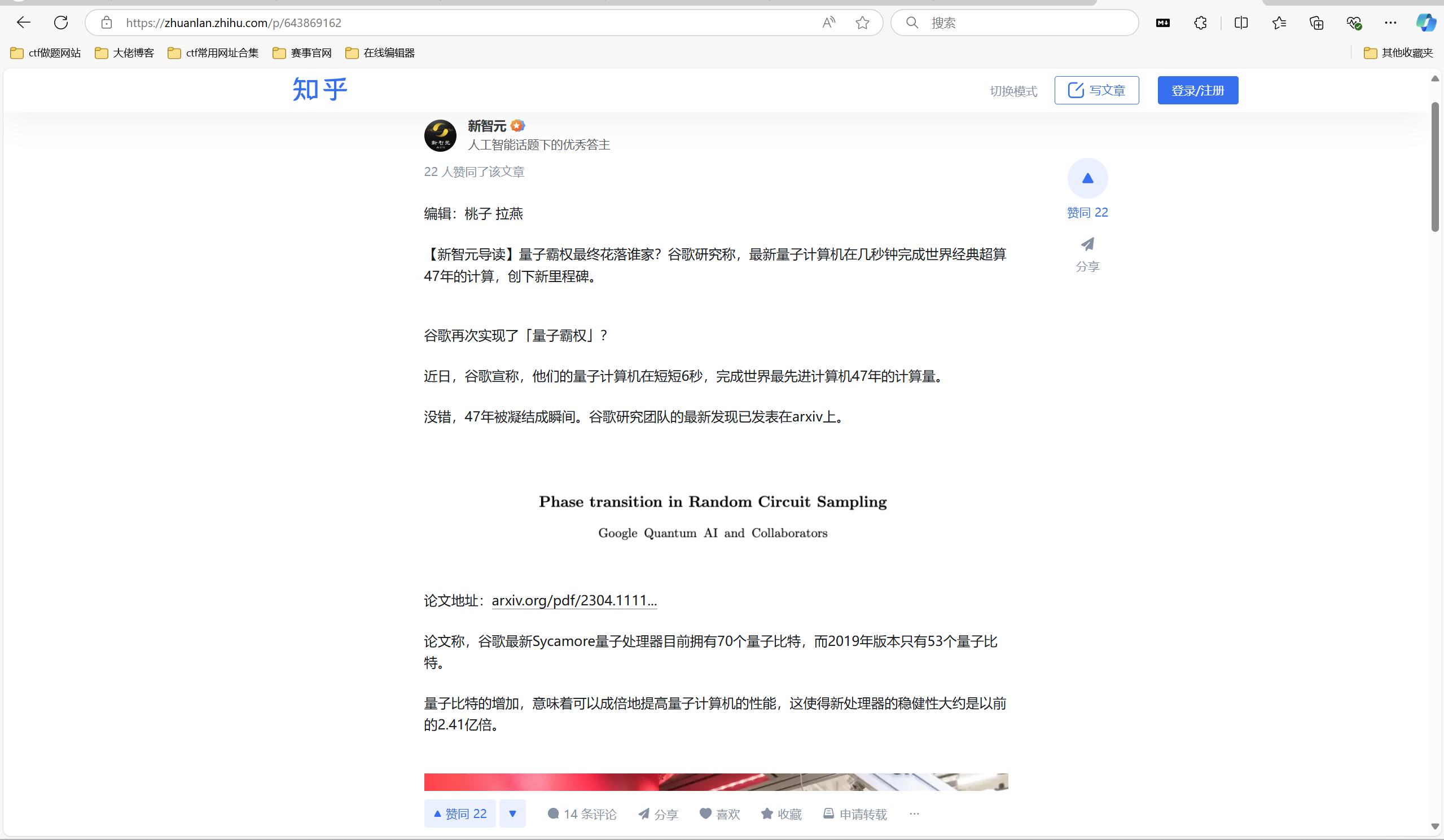
搜索关键词看到这篇文章
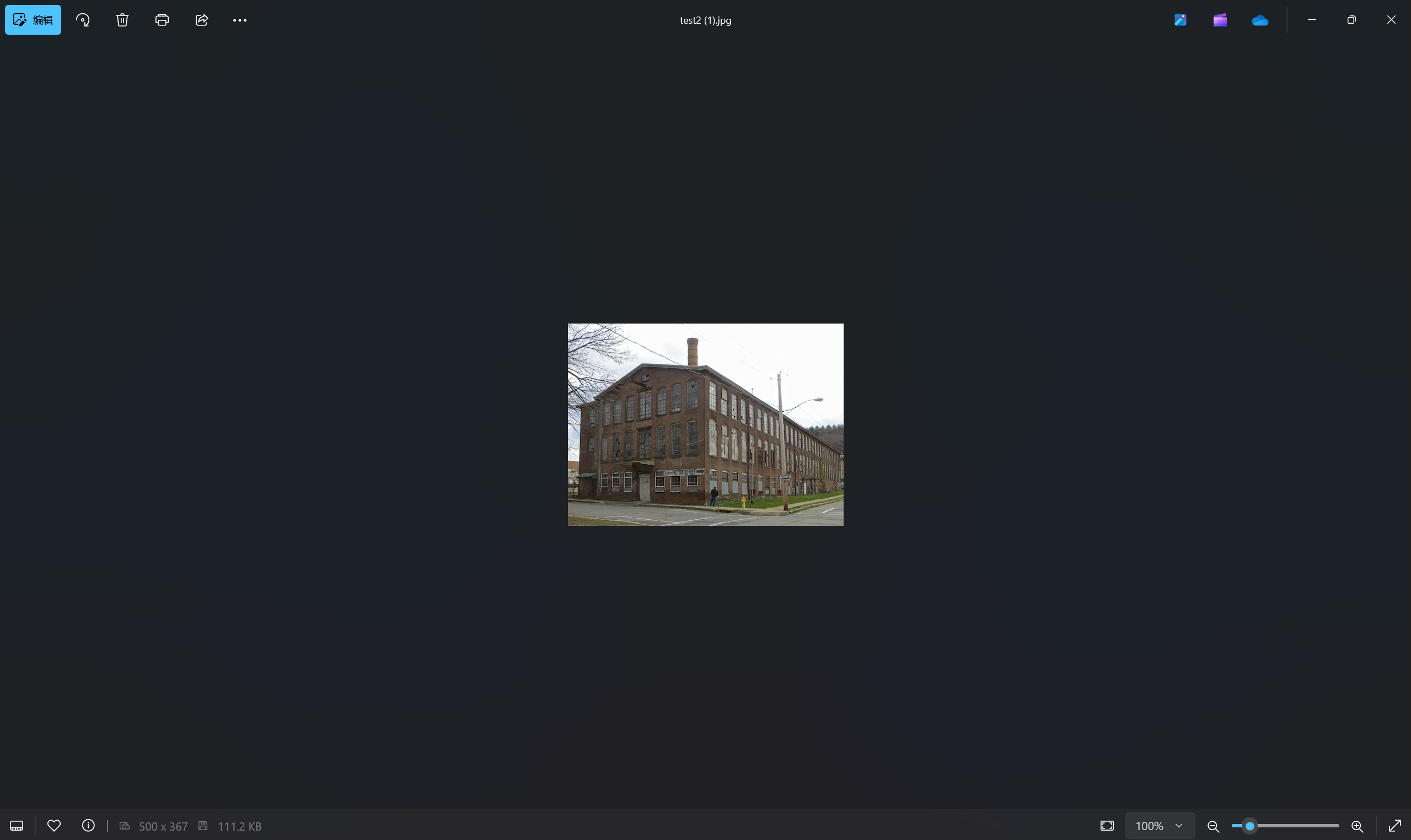
快来社我_3
下载附件
这好熟悉,有点像某个数列
下载附件
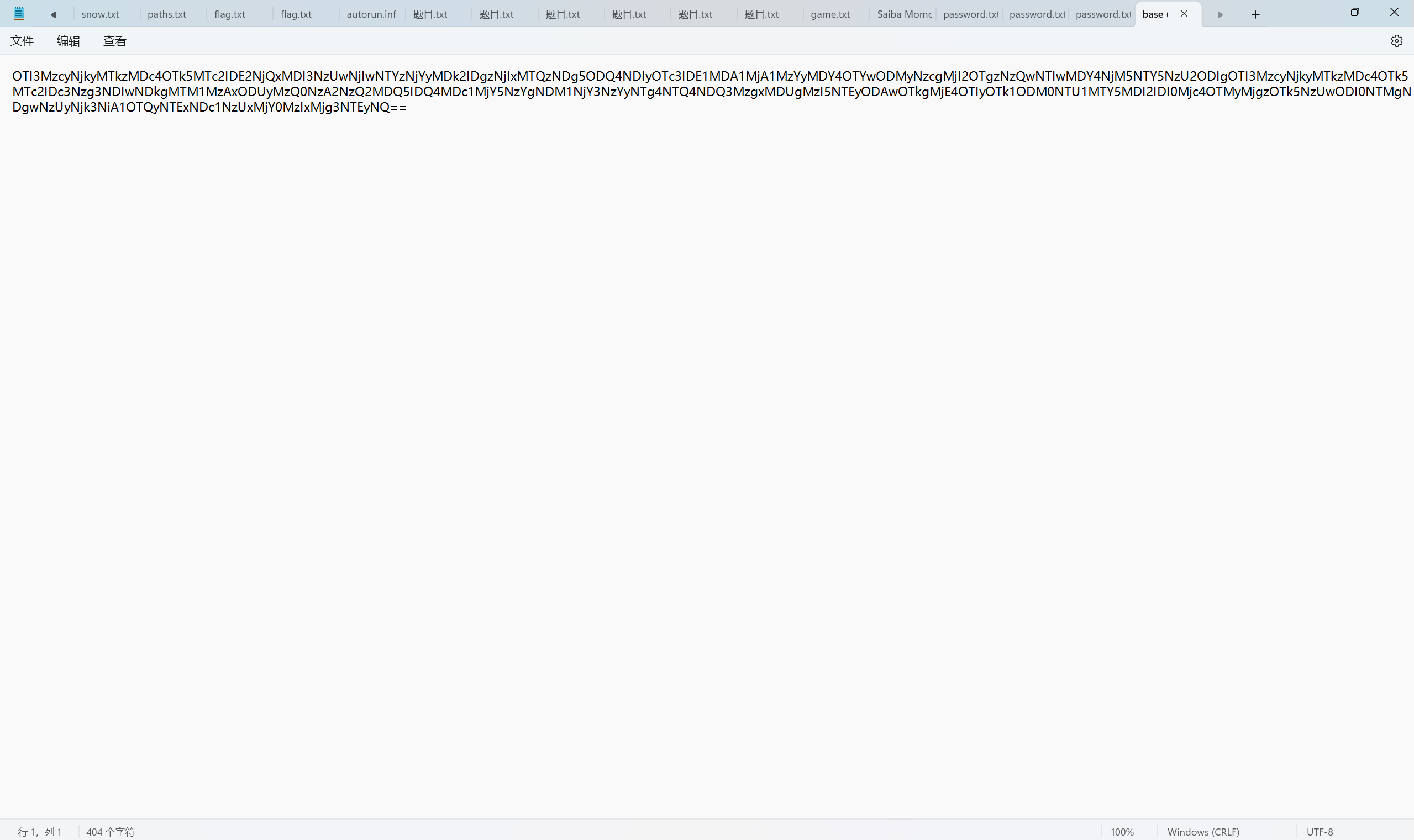
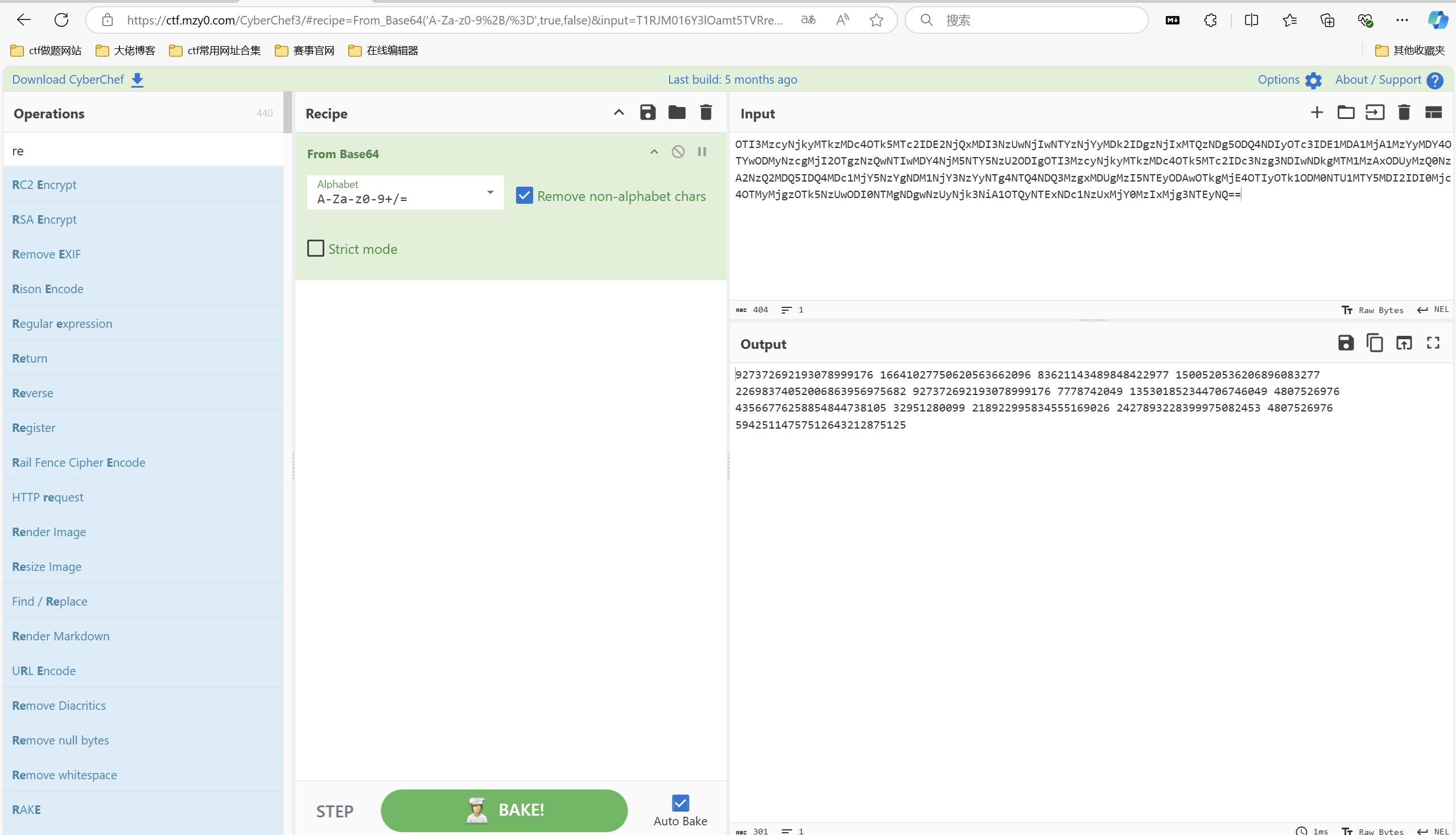
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 from Crypto.Util.number import * ls=[927372692193078999176,16641027750620563662096,83621143489848422977,1500520536206896083277,22698374052006863956975682,927372692193078999176,7778742049,135301852344706746049,4807526976,43566776258854844738105,32951280099,218922995834555169026,2427893228399975082453,4807526976,59425114757512643212875125] def find_fibonacci_index(number): if number < 0: return -1 a, b = 0, 1 index = 1 while b < number: a, b = b, a + b index += 1 if b == number: return index else: return -1 ans=[] for i in ls: position = find_fibonacci_index(i) if position != -1: ans.append(position) print(''.join(chr(i) for i in ans))
运行得到
好奇怪的图像
下载附件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 import cv2 from PIL import Image img1 = cv2.imread(r'E:\\qiguai\\test.jpg',-1) # print(img1) print(img1.shape) new_img = [] for i in range(0,len(img1[0]),23*2*2): img = img1[0][i:i+23*2*2] new_img += [img] # print(len(new_img)) x = len(new_img) y = len(new_img[0]) im = Image.new("RGB", (x, y)) for i in range(0, x): for j in range(0, y): im.putpixel((i, j), (new_img[i][j][0], new_img[i][j][1], new_img[i] [j][2])) im.save("E:\\qiguai\\flag.png")
运行得到
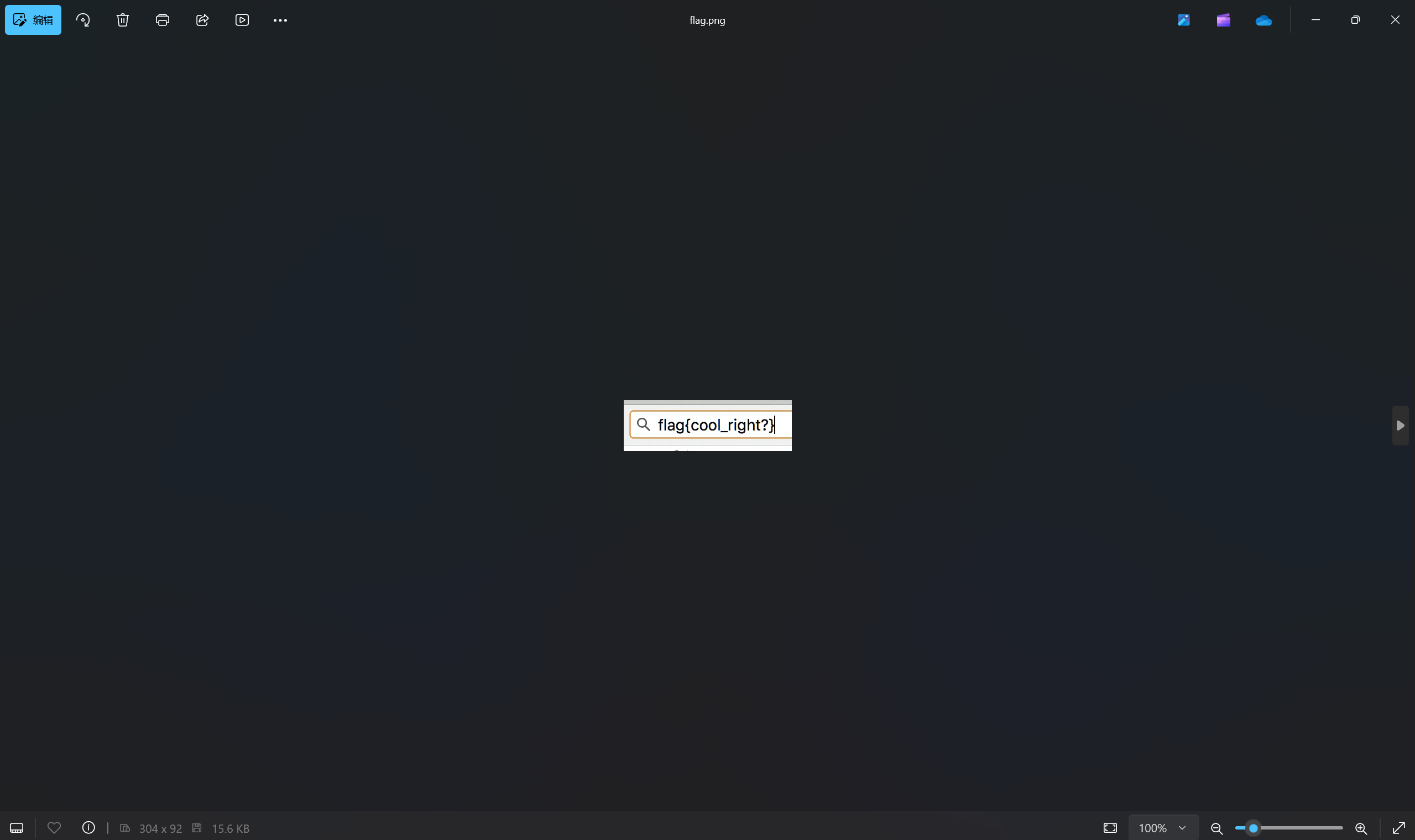
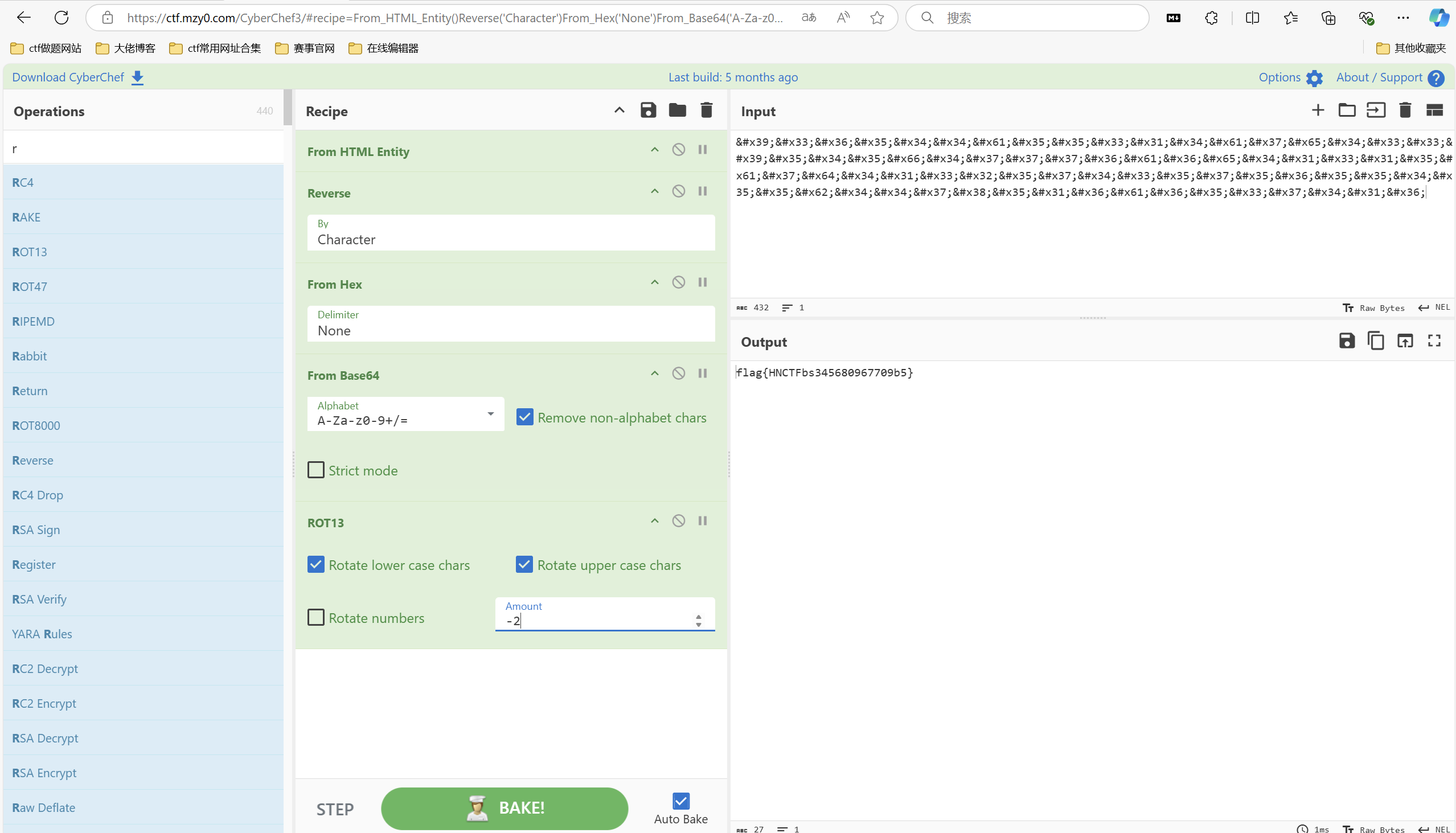
啥玩意啊这
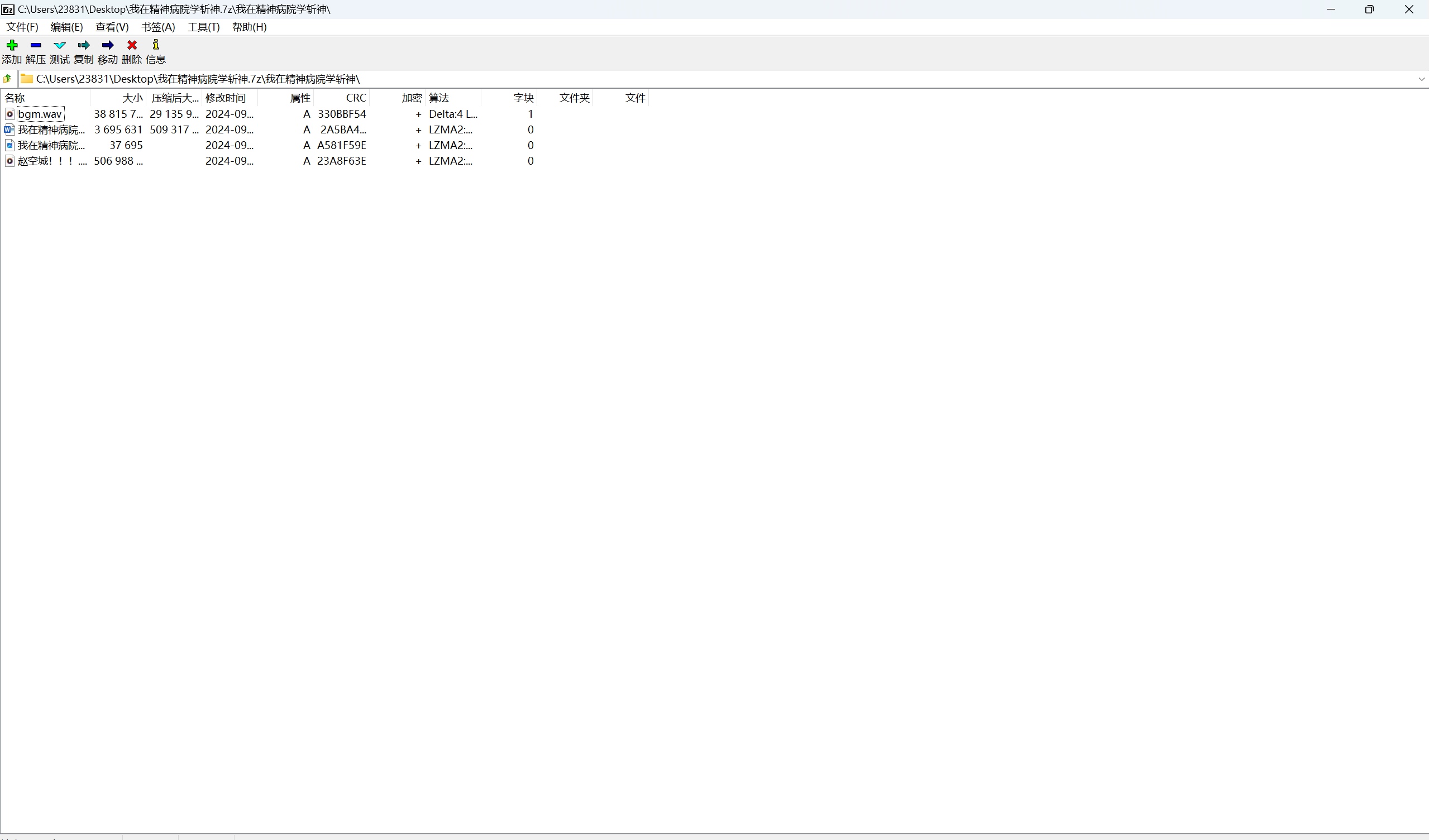
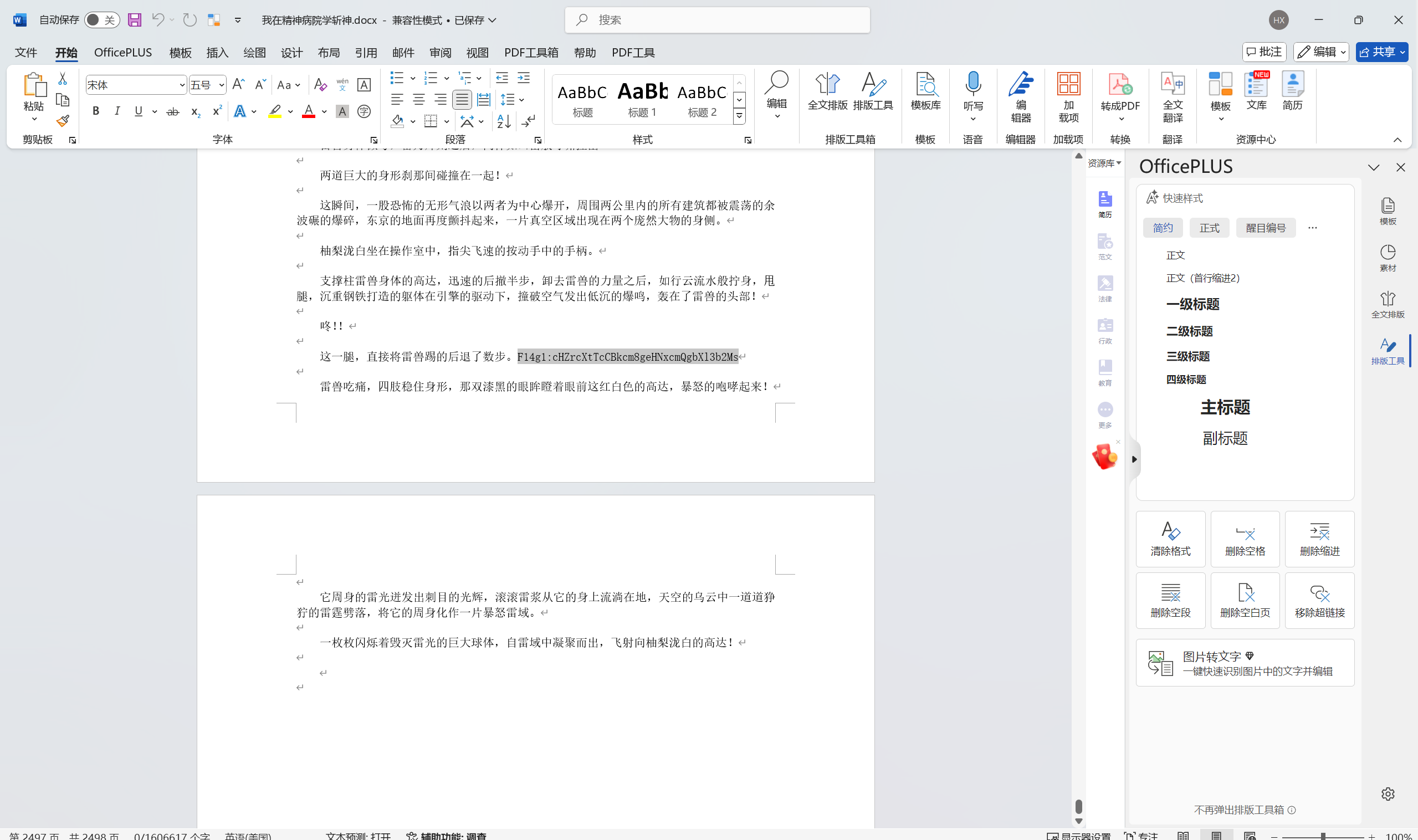
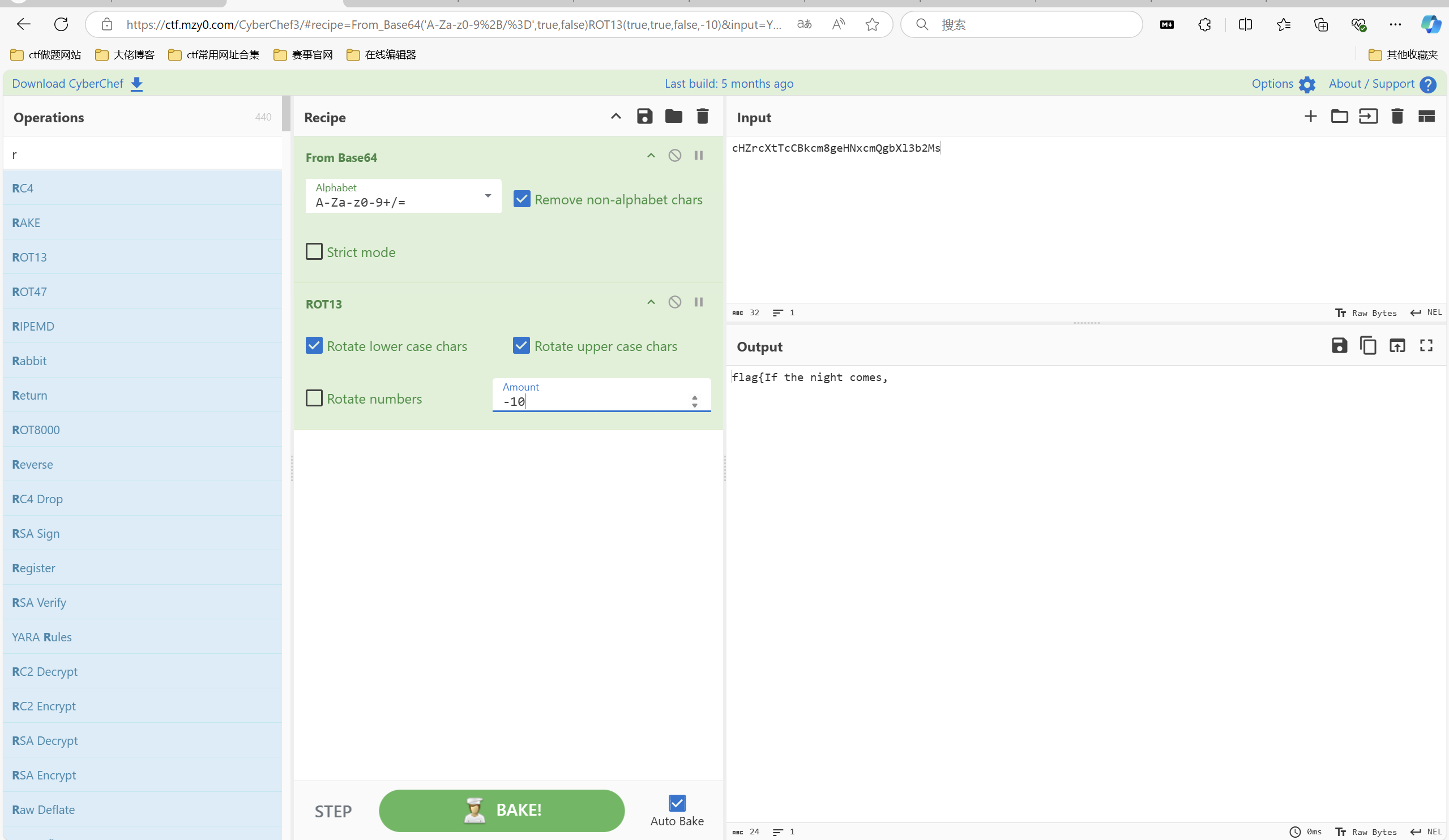
我在精神病院学斩神
flag2
flag3
flag4
提交解出flag的每句话最后一个单词
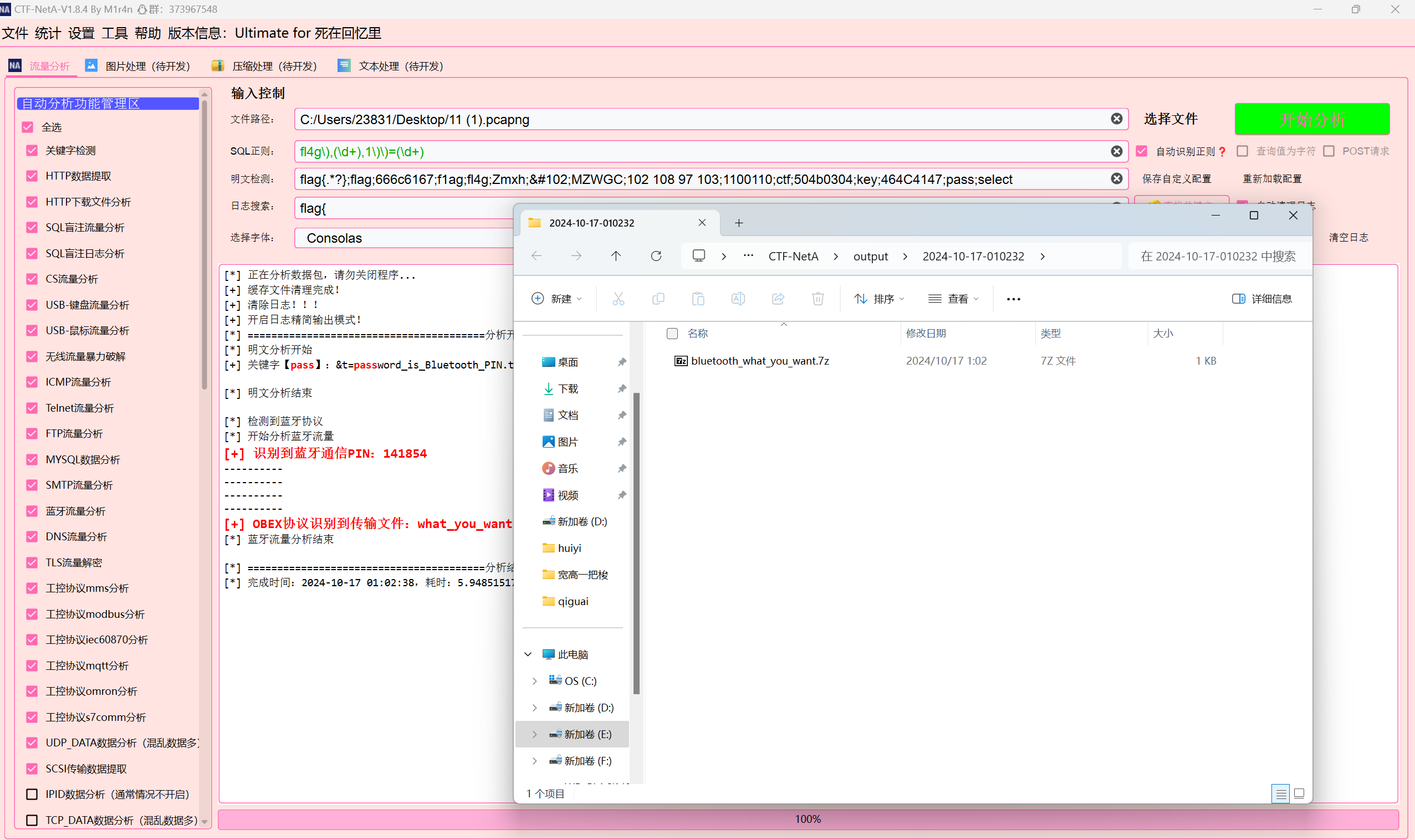
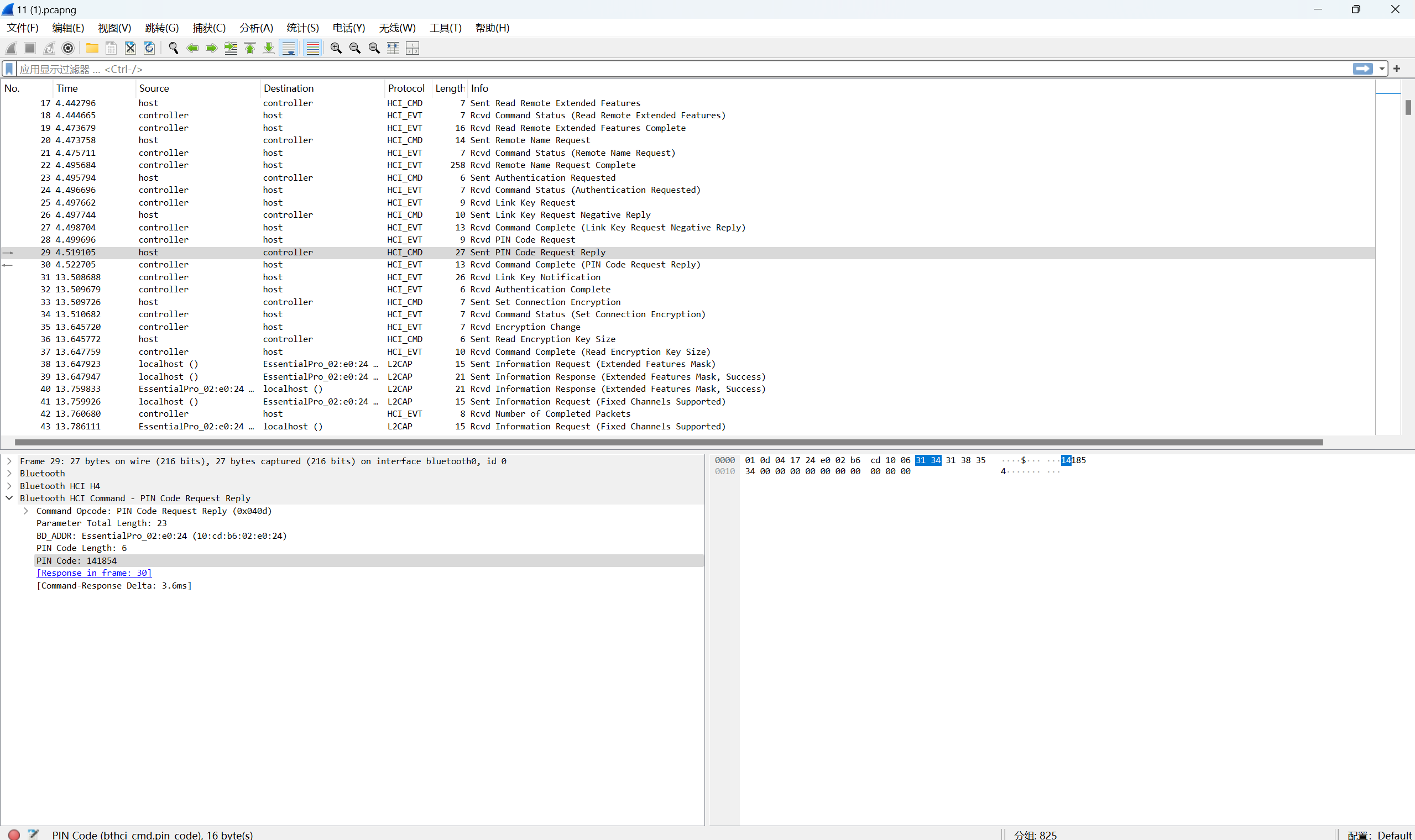
流量分析1
签退